Wireshark 64 2 6 3 0 0
Author: b | 2025-04-24
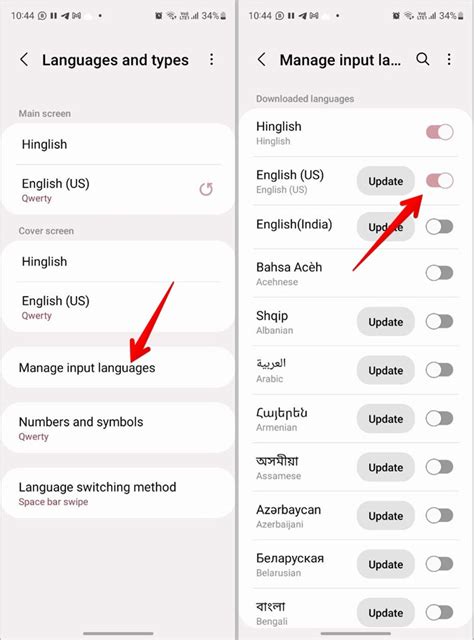
practica 3 Herramienta Wireshark y lanspy 2 0 / 0 1 2 3 4 5 . 4 5 / 6 3 0 1 6 3 . / 0 1 2 3 4 5 . 4 5 / 6 3 0 1 6 3
0 0 0 3 5 4 0 0 1 3 3 4 4 0 0 0 0 3 3 3 1 0 3 6 1 0 0 - fill-a
RunningNow we can compile this and link it, by runninggcc -c -o main.o -I../picotcp/build/include main.cgcc -o main.elf main.o ../picotcp/build/lib/libpicotcp.aNext we'll create a persistent tap device - a virtual network port. You don't need to repeat this each time, the device will exist until you reboot, or until you go sudo tunctl -d tap0sudo ifconfig tap0 192.168.5.5">sudo tunctl -u username>sudo ifconfig tap0 192.168.5.5Now, you should be able to run ./main.elf, and see output likeProtocol ethernet registered (layer: 2).Protocol ipv4 registered (layer: 3).Protocol ipv6 registered (layer: 3).Protocol icmp4 registered (layer: 4).Protocol icmp6 registered (layer: 4).Protocol igmp registered (layer: 4).Protocol udp registered (layer: 4).Protocol tcp registered (layer: 4).Device tap0 created.Assigned ipv4 192.168.5.4 to device tap0starting ping64 bytes from 192.168.5.5: icmp_req=1 ttl=64 time=5 ms64 bytes from 192.168.5.5: icmp_req=2 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=3 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=4 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=5 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=6 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=7 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=8 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=9 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=10 ttl=64 time=0 msfinished !While the application is running, you can also runto send pings in the other direction.Investigating what happenedRun wireshark, and sniff the tap0 interface. Then run the ./main.elf again, and see what happens. You should see an ARP request from picoTCP to Linux, and a reply. After that you should see the ping requests and replies going back and forth.Note, sometimes you may see lots of other stuff, practica 3 Herramienta Wireshark y lanspy 2 0 3 0googleDmg Canvas 3 0 2 Download Free UtorrentDownload GLC-Player for free. GLCPlayer is a OpenGL Open Source 3D viewer used to view 3d models (COLLADA, 3DXML, OBJ 3DS STL OFF COFF Format) and to navigate easily in these models. Verify Downloads. File hashes for the 3.2.7 release can be found in the signatures file. It is signed with key id 0xE6FEAEEA. Prior to April 2016 downloads were signed with key id 0x21F2949A. Wireshark is subject to U.S. Export regulations. Consult a lawyer if you have any questions.Download file - DMGCanvas3.0.6.zip. FAST INSTANT DOWNLOAD Download type. DMG Canvas creates disk images (.dmg). The imaging procedure consists of simply dragging and dropping the required files into the application window. As a background, you can use a file created in the graphical editor. You will immediately see the result as it appears in the Finder. Click the Build button to create the finished image.Download Wireshark The current stable release of Wireshark is 3.2.7. Adobe xd 24 3 22. It supersedes all previous releases. You can also download the latest development release (3.3.1) and documentation. Windows Installer (64-bit)Windows Installer (32-bit)Windows PortableApps® (32-bit)macOS Intel 64-bit .dmgSource CodeWindows Installer (64-bit)Windows Installer (32-bit)Windows PortableApps® (32-bit)macOS Intel 64-bit .dmgSource CodeWindows Installer (64-bit)Windows Installer (32-bit)Windows PortableApps® (32-bit)macOS Intel 64-bit .dmgSource CodeOlder Releases All present and past releases can be found in our download area. Installation Notes For a complete list of system requirements and supported platforms, please consult the User's Guide. Information about each release can be found in the release notes. Each Windows package comes with the latest stable release of Npcap, which is required for live packet capture. If needed you can download separately from the Npcap web site. You can also capture packets using WinPcap, although it is no longer maintained or supported. Live on the Bleeding Edge You can download source code packages and Windows installers which are automatically created each time code is checked into the source code repository. These packages are available in the automated build section of our download area. Go Spelunking3 0googleStay Current You can stay informed about new Wireshark releases by subscribing to the wireshark-announce mailing list. We also provide a PAD file to make automated checking easier. Verify Downloads File hashes for the 3.2.7 release can be found in the signatures file. It is signed with key id 0xE6FEAEEA. Prior to April 2016 downloads were signed with key id 0x21F2949A. Stay Legal Wireshark is subject to U.S. export regulations. Take heed. Consult a lawyer if you have any questions. I have a lot of traffic..ANSWER: SteelCentral™ AppResponse 11• Full stack analysis – from packets to pages• Rich performance metrics & pre-defined insights for fast problem identification/resolution• Modular, flexible solution for deeply-analyzing network & application performanceLearn More Wireshark packages are available for most platforms, including the ones listed below. One switch 1 6 2.Standard package: Wireshark is available via the default packaging system on that platform. Vendor / PlatformSourcesAlpine / Alpine LinuxStandard packageApple / macOSHomebrew(Formula)MacPortsFinkArch Linux / Arch LinuxStandardComments
RunningNow we can compile this and link it, by runninggcc -c -o main.o -I../picotcp/build/include main.cgcc -o main.elf main.o ../picotcp/build/lib/libpicotcp.aNext we'll create a persistent tap device - a virtual network port. You don't need to repeat this each time, the device will exist until you reboot, or until you go sudo tunctl -d tap0sudo ifconfig tap0 192.168.5.5">sudo tunctl -u username>sudo ifconfig tap0 192.168.5.5Now, you should be able to run ./main.elf, and see output likeProtocol ethernet registered (layer: 2).Protocol ipv4 registered (layer: 3).Protocol ipv6 registered (layer: 3).Protocol icmp4 registered (layer: 4).Protocol icmp6 registered (layer: 4).Protocol igmp registered (layer: 4).Protocol udp registered (layer: 4).Protocol tcp registered (layer: 4).Device tap0 created.Assigned ipv4 192.168.5.4 to device tap0starting ping64 bytes from 192.168.5.5: icmp_req=1 ttl=64 time=5 ms64 bytes from 192.168.5.5: icmp_req=2 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=3 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=4 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=5 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=6 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=7 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=8 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=9 ttl=64 time=0 ms64 bytes from 192.168.5.5: icmp_req=10 ttl=64 time=0 msfinished !While the application is running, you can also runto send pings in the other direction.Investigating what happenedRun wireshark, and sniff the tap0 interface. Then run the ./main.elf again, and see what happens. You should see an ARP request from picoTCP to Linux, and a reply. After that you should see the ping requests and replies going back and forth.Note, sometimes you may see lots of other stuff,
2025-03-283 0googleDmg Canvas 3 0 2 Download Free UtorrentDownload GLC-Player for free. GLCPlayer is a OpenGL Open Source 3D viewer used to view 3d models (COLLADA, 3DXML, OBJ 3DS STL OFF COFF Format) and to navigate easily in these models. Verify Downloads. File hashes for the 3.2.7 release can be found in the signatures file. It is signed with key id 0xE6FEAEEA. Prior to April 2016 downloads were signed with key id 0x21F2949A. Wireshark is subject to U.S. Export regulations. Consult a lawyer if you have any questions.Download file - DMGCanvas3.0.6.zip. FAST INSTANT DOWNLOAD Download type. DMG Canvas creates disk images (.dmg). The imaging procedure consists of simply dragging and dropping the required files into the application window. As a background, you can use a file created in the graphical editor. You will immediately see the result as it appears in the Finder. Click the Build button to create the finished image.Download Wireshark The current stable release of Wireshark is 3.2.7. Adobe xd 24 3 22. It supersedes all previous releases. You can also download the latest development release (3.3.1) and documentation. Windows Installer (64-bit)Windows Installer (32-bit)Windows PortableApps® (32-bit)macOS Intel 64-bit .dmgSource CodeWindows Installer (64-bit)Windows Installer (32-bit)Windows PortableApps® (32-bit)macOS Intel 64-bit .dmgSource CodeWindows Installer (64-bit)Windows Installer (32-bit)Windows PortableApps® (32-bit)macOS Intel 64-bit .dmgSource CodeOlder Releases All present and past releases can be found in our download area. Installation Notes For a complete list of system requirements and supported platforms, please consult the User's Guide. Information about each release can be found in the release notes. Each Windows package comes with the latest stable release of Npcap, which is required for live packet capture. If needed you can download separately from the Npcap web site. You can also capture packets using WinPcap, although it is no longer maintained or supported. Live on the Bleeding Edge You can download source code packages and Windows installers which are automatically created each time code is checked into the source code repository. These packages are available in the automated build section of our download area. Go Spelunking3 0googleStay Current You can stay informed about new Wireshark releases by subscribing to the wireshark-announce mailing list. We also provide a PAD file to make automated checking easier. Verify Downloads File hashes for the 3.2.7 release can be found in the signatures file. It is signed with key id 0xE6FEAEEA. Prior to April 2016 downloads were signed with key id 0x21F2949A. Stay Legal Wireshark is subject to U.S. export regulations. Take heed. Consult a lawyer if you have any questions. I have a lot of traffic..ANSWER: SteelCentral™ AppResponse 11• Full stack analysis – from packets to pages• Rich performance metrics & pre-defined insights for fast problem identification/resolution• Modular, flexible solution for deeply-analyzing network & application performanceLearn More Wireshark packages are available for most platforms, including the ones listed below. One switch 1 6 2.Standard package: Wireshark is available via the default packaging system on that platform. Vendor / PlatformSourcesAlpine / Alpine LinuxStandard packageApple / macOSHomebrew(Formula)MacPortsFinkArch Linux / Arch LinuxStandard
2025-04-02Download Wireshark 4.4.5 (64-bit) Date released: 25 Feb 2025 (2 weeks ago) Download Wireshark 4.4.4 (64-bit) Date released: 20 Feb 2025 (3 weeks ago) Download Wireshark 4.4.3 (64-bit) Date released: 09 Jan 2025 (2 months ago) Download Wireshark 4.4.2 (64-bit) Date released: 21 Nov 2024 (4 months ago) Download Wireshark 4.4.1 (64-bit) Date released: 10 Oct 2024 (5 months ago) Download Wireshark 4.4.0 (64-bit) Date released: 29 Aug 2024 (7 months ago) Download Wireshark 4.2.6 (64-bit) Date released: 11 Jul 2024 (8 months ago) Download Wireshark 4.2.5 (64-bit) Date released: 16 May 2024 (10 months ago) Download Wireshark 4.2.4 (64-bit) Date released: 28 Mar 2024 (12 months ago) Download Wireshark 4.2.3 (64-bit) Date released: 15 Feb 2024 (one year ago) Download Wireshark 4.2.2 (64-bit) Date released: 05 Jan 2024 (one year ago) Download Wireshark 4.2.1 (64-bit) Date released: 04 Jan 2024 (one year ago) Download Wireshark 4.2.0 (64-bit) Date released: 17 Nov 2023 (one year ago) Download Wireshark 4.0.10 (64-bit) Date released: 05 Oct 2023 (one year ago) Download Wireshark 4.0.8 (64-bit) Date released: 24 Aug 2023 (one year ago) Download Wireshark 4.0.7 (64-bit) Date released: 13 Jul 2023 (one year ago) Download Wireshark 4.0.6 (64-bit) Date released: 25 May 2023 (one year ago) Download Wireshark 4.0.5 (64-bit) Date released: 13 Apr 2023 (one year ago) Download Wireshark 4.0.4 (64-bit) Date released: 03 Mar 2023 (2 years ago) Download Wireshark 4.0.3 (64-bit) Date released: 19 Jan 2023 (2 years ago)
2025-03-25Download Wireshark 4.4.5 (64-bit) Date released: 25 Feb 2025 (3 weeks ago) Download Wireshark 4.4.4 (64-bit) Date released: 20 Feb 2025 (4 weeks ago) Download Wireshark 4.4.3 (64-bit) Date released: 09 Jan 2025 (2 months ago) Download Wireshark 4.4.2 (64-bit) Date released: 21 Nov 2024 (4 months ago) Download Wireshark 4.4.1 (64-bit) Date released: 10 Oct 2024 (5 months ago) Download Wireshark 4.4.0 (64-bit) Date released: 29 Aug 2024 (7 months ago) Download Wireshark 4.2.6 (64-bit) Date released: 11 Jul 2024 (8 months ago) Download Wireshark 4.2.5 (64-bit) Date released: 16 May 2024 (10 months ago) Download Wireshark 4.2.4 (64-bit) Date released: 28 Mar 2024 (12 months ago) Download Wireshark 4.2.3 (64-bit) Date released: 15 Feb 2024 (one year ago) Download Wireshark 4.2.2 (64-bit) Date released: 05 Jan 2024 (one year ago) Download Wireshark 4.2.1 (64-bit) Date released: 04 Jan 2024 (one year ago) Download Wireshark 4.2.0 (64-bit) Date released: 17 Nov 2023 (one year ago) Download Wireshark 4.0.10 (64-bit) Date released: 05 Oct 2023 (one year ago) Download Wireshark 4.0.8 (64-bit) Date released: 24 Aug 2023 (one year ago) Download Wireshark 4.0.7 (64-bit) Date released: 13 Jul 2023 (one year ago) Download Wireshark 4.0.6 (64-bit) Date released: 25 May 2023 (one year ago) Download Wireshark 4.0.5 (64-bit) Date released: 13 Apr 2023 (one year ago) Download Wireshark 4.0.4 (64-bit) Date released: 03 Mar 2023 (2 years ago) Download Wireshark 4.0.3 (64-bit) Date released: 19 Jan 2023 (2 years ago)
2025-04-15More than 5 years have passed since last update.snmptrapの発報用方法監視サーバ(zabbix等)で、SNMPTRAP受信をテスト(Trigger試験)することがありました。その際、SNMPTRAPを容易に発報できる仕組みがあればと思い手順をまとめました。特に、version1はトラップ送信元IPアドレス(AgentAddress)を指定できるので便利です。今回取り上げるトラップの種類今回実施したサンプルの設定値皆さんの環境に合わせて置き換えてくださいVersionコミュニティ名1publicv12cpublicv23publicv3(共通)トラップ宛先IP = 192.168.10.189(snmptrapd稼働IP)(共通)トラップするOID = netSnmpExperimental.1=hogehoge1,netSnmpExperimental.2=hogehoge2version1用設定内容GenericTrapType = EnterpriseSpecific(6)SpecificTrapType = 99AgentAddressを指定して、送信元IP=10.0.0.1に詐称version3用設定内容EngineID = 0x80001F88803C41A86E8BCE0D59認証/暗号化有無 = Auth/NoPrivユーザ名 = publicv3認証用パスワード(SHA) = hogehoge123snmptrap受信側設定snmptrapのversion1,2c,3を受信できるように設定/etc/snmp/snmptrapd.confauthCommunity log,execute,net publicv1authCommunity log,execute,net publicv2authUser log,execute,net publicv3createUser -e 0x80001F88803C41A86E8BCE0D59 publicv3 SHA hogehoge123snmptrap v1 送信設定コマンドと実行結果version1は、agent addressが引数にあるので、任意のアドレスをSNMPTRAP送信元に定義することができるのでテストが簡単になります。ここでは、10.0.0.1を送信元アドレスとして定義してみます。snmptrap(v1)snmptrap -v 1 -c publicv1 192.168.10.189 '' 10.0.0.1 6 99 '' netSnmpExperimental.1 s "hogehoge1" netSnmpExperimental.2 s "hogehoge2"log(v1)May 6 20:22:47 localhost snmptrapd[2107]: 2017-05-06 20:22:47 10.0.0.1(via UDP: [192.168.10.189]:35025->[192.168.10.189]:162) TRAP, SNMP v1, community publicv1#012#011SNMPv2-SMI::enterprises.3.1.1 Enterprise Specific Trap (99) Uptime: 1:24:44.66#012#011NET-SNMP-MIB::netSnmpExperimental.1 = STRING: "hogehoge1"#011NET-SNMP-MIB::netSnmpExperimental.2 = STRING: "hogehoge2"wiresharkのログ(v1)Simple Network Management Protocol version: version-1 (0) community: publicv1 data: trap (4) trap enterprise: 1.3.6.1.4.1.3.1.1 (iso.3.6.1.4.1.3.1.1) agent-addr: 10.0.0.1 (10.0.0.1) ← 送信元アドレス詐称できてます generic-trap: enterpriseSpecific (6) specific-trap: 99 time-stamp: 508466 variable-bindings: 2 items 1.3.6.1.4.1.8072.9999.1: 686f6765686f676531 Object Name: 1.3.6.1.4.1.8072.9999.1 (iso.3.6.1.4.1.8072.9999.1) Value (OctetString): 686f6765686f676531 1.3.6.1.4.1.8072.9999.2: 686f6765686f676532 Object Name: 1.3.6.1.4.1.8072.9999.2 (iso.3.6.1.4.1.8072.9999.2) Value (OctetString): 686f6765686f676532snmptrap v2c 送信設定コマンドと実行結果snmptrap(v2c)snmptrap -v 2c -c publicv2 192.168.10.189 '' netSnmpExperimental netSnmpExperimental.1 s "hogehoge1" netSnmpExperimental.2 s "hogehoge2"log(v2c)May 6 19:16:48 localhost snmptrapd[2107]: 2017-05-06 19:16:48 localhost.localdomain [UDP: [192.168.10.189]:53862->[192.168.10.189]:162]:#012DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (112564) 0:18:45.64#011SNMPv2-MIB::snmpTrapOID.0 = OID: NET-SNMP-MIB::netSnmpExperimental#011NET-SNMP-MIB::netSnmpExperimental.1 = STRING: "hogehoge1"#011NET-SNMP-MIB::netSnmpExperimental.2 = STRING: "hogehoge2"wiresharkのログ(v2c)Simple Network Management Protocol version: v2c (1) community: publicv2 data: snmpV2-trap (7) snmpV2-trap request-id: 203283761 error-status: noError (0) error-index: 0 variable-bindings: 4 items 1.3.6.1.2.1.1.3.0: 112564 sysUpTime(共通) Object Name: 1.3.6.1.2.1.1.3.0 (iso.3.6.1.2.1.1.3.0) Value (Timeticks): 112564 1.3.6.1.6.3.1.1.4.1.0: 1.3.6.1.4.1.8072.9999 (iso.3.6.1.4.1.8072.9999) snmpTrapOID(共通) Object Name: 1.3.6.1.6.3.1.1.4.1.0 (iso.3.6.1.6.3.1.1.4.1.0) Value (OID): 1.3.6.1.4.1.8072.9999 (iso.3.6.1.4.1.8072.9999) 1.3.6.1.4.1.8072.9999.1: 686f6765686f676531 Object Name: 1.3.6.1.4.1.8072.9999.1 (iso.3.6.1.4.1.8072.9999.1) Value (OctetString): 686f6765686f676531 1.3.6.1.4.1.8072.9999.2: 686f6765686f676532 Object Name: 1.3.6.1.4.1.8072.9999.2 (iso.3.6.1.4.1.8072.9999.2) Value (OctetString): 686f6765686f676532snmptrap v3 送信設定コマンドと実行結果snmptrap(v3)snmptrap -e 0x80001F88803C41A86E8BCE0D59 -v 3 -l authNoPriv -u publicv3 -a SHA -A hogehoge123 192.168.10.189 '' netSnmpExperimental netSnmpExperimental.1 s 'hogehoge1' netSnmpExperimental.2 s 'hogehoge2'log(v3)May 6 19:19:00 localhost snmptrapd[2107]: 2017-05-06 19:19:00 localhost.localdomain [UDP: [192.168.10.189]:46755->[192.168.10.189]:162]:#012DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (125758) 0:20:57.58#011SNMPv2-MIB::snmpTrapOID.0 = OID: NET-SNMP-MIB::netSnmpExperimental#011NET-SNMP-MIB::netSnmpExperimental.1 = STRING: "hogehoge1"#011NET-SNMP-MIB::netSnmpExperimental.2 = STRING: "hogehoge2"wiresharkのログ(v3)Simple Network Management Protocol msgVersion: snmpv3 (3) msgGlobalData msgID: 453410534 msgMaxSize: 65507 msgFlags: 01 .... .0.. = Reportable: Not set .... ..0. = Encrypted: Not set .... ...1 = Authenticated: Set msgSecurityModel: USM (3) msgAuthoritativeEngineID: 80001f88803c41a86e8bce0d59 1... .... = Engine ID Conformance: RFC3411 (SNMPv3) Engine Enterprise ID: net-snmp (8072) Engine ID Format: Reserved/Enterprise-specific (128): Net-SNMP Random Engine ID Data: 3c41a86e Engine ID Data: Creation Time: May 6, 2017 09:24:27 EDT msgAuthoritativeEngineBoots: 0 msgAuthoritativeEngineTime: 0 msgUserName: publicv3 msgAuthenticationParameters: c097fbc636a1334c5bcf37f3
2025-03-27