Vpn site
Author: h | 2025-04-24
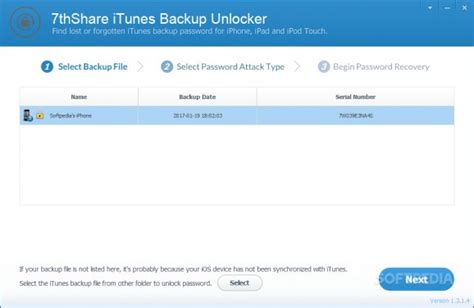
FortiGate Site to Site VPN Configuration, FortiGate IPsec VPN Site to Site Configuration, How to Configure IPsec VPN Site to Site on FortiGate, ipsec vpn on Site-to-Site VPN License Register free Synology Site-to-Site VPN licenses to activate the Site-to-Site VPN feature in VPN Plus Server. Site-to-Site VPN lets companies and organizations establish encrypted tunnels over the internet
What is AWS Site-to-Site VPN? - AWS Site-to-Site VPN
EIGRP MPLS VPN PE-CE Site of Origin The EIGRP MPLS VPN PE-CE Site of Origin feature introduces the capability to filter Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) traffic on a per-site basis for Enhanced Interior Gateway Routing Protocol (EIGRP) networks. Site of Origin (SoO) filtering is configured at the interface level and is used to manage MPLS VPN traffic and to prevent transient routing loops from occurring in complex and mixed network topologies. This feature is designed to support the MPLS VPN Support for EIGRP Between Provider Edge (PE) and Customer Edge (CE) feature. Support for backdoor links is provided by this feature when installed on PE routers that support EIGRP MPLS VPNs. Finding Feature InformationPrerequisites for EIGRP MPLS VPN PE-CE Site of OriginRestrictions for EIGRP MPLS VPN PE-CE Site of OriginInformation About EIGRP MPLS VPN PE-CE Site of OriginHow to Configure EIGRP MPLS VPN PE-CE Site of Origin SupportConfiguration Examples for EIGRP MPLS VPN PE-CE SoOAdditional ReferencesFeature Information for EIGRP MPLS VPN PE-CE Site of OriginGlossaryFinding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. Prerequisites for EIGRP MPLS VPN PE-CE Site of OriginThis document assumes that Border Gateway Protocol (BGP) is configured in the network core (or the service provider backbone). The following tasks will also need to be completed before you can configure this feature:This feature was introduced to support the MPLS VPN Support for EIGRP Between Provider Edge and Customer Edge feature and should be configured after the EIGRP MPLS VPN is created. All PE routers that are configured to support the EIGRP MPLS VPN must run Cisco IOS XE Release 2.1 or a later release, which provides support for the SoO extended community.Restrictions for EIGRP MPLS VPN PE-CE Site of OriginIf a VPN site is partitioned and the SoO extended community attribute is configured on a backdoor router interface, the backdoor link cannot be used as an alternate path to reach prefixes originated in other partitions of the same site. A unique SoO value must be configured for each individual VPN site. The same value must be configured on all provider edge and customer edge interfaces (if SoO is configured on the CE routers) that support the same VPN site. Information About EIGRP MPLS VPN PE-CE Site of OriginEIGRP MPLS VPN PE-CE Site of Origin Support OverviewSite of Origin Support for Backdoor LinksRouter Interoperation with the Site of Origin Extended CommunityRedistribution of BGP VPN Routes That Carry the Site of Origin into EIGRPBGP Cost Community Support for When traffic is idle?This behavior is expected for policy-based (also known as static routing) VPN gateways. When the traffic over the tunnel is idle for more than five minutes, the tunnel is torn down. When traffic starts flowing in either direction, the tunnel is reestablished immediately.Can I use software VPNs to connect to Azure?We support Windows Server 2012 Routing and Remote Access servers for site-to-site cross-premises configuration.Other software VPN solutions should work with the gateway, as long as they conform to industry-standard IPsec implementations. For configuration and support instructions, contact the vendor of the software.Can I connect to a VPN gateway via point-to-site when located at a site that has an active site-to-site connection?Yes, but the public IP addresses of the point-to-site client must be different from the public IP addresses that the site-to-site VPN device uses, or else the point-to-site connection won't work. Point-to-site connections with IKEv2 can't be initiated from the same public IP addresses where a site-to-site VPN connection is configured on the same VPN gateway.Point-to-site connectionsHow many VPN client endpoints can I have in my point-to-site configuration?It depends on the gateway SKU. For more information on the supported number of connections, see Gateway SKUs.What client operating systems can I use with point-to-site?The following client operating systems are supported:Windows Server 2008 R2 (64-bit only)Windows 8.1 (32-bit and 64-bit)Windows Server 2012 (64-bit only)Windows Server 2012 R2 (64-bit only)Windows Server 2016 (64-bit only)Windows Server 2019 (64-bit only)Windows Server 2022 (64-bit only)Windows 10Windows 11macOS version 10.11 or laterLinux (strongSwan)iOSCan I traverse proxies and firewalls by using point-to-site capability?Azure supports three types of point-to-site VPN options:Secure Socket Tunneling Protocol (SSTP): A Microsoft proprietary SSL-based solution that can penetrate firewalls because most firewalls open the outbound TCP port that 443 SSL uses.OpenVPN: A SSL-based solution that can penetrate firewalls because most firewalls open the outbound TCP port that 443 SSL uses.IKEv2 VPN: A standards-based IPsec VPN solution that uses outbound UDP ports 500 and 4500, along with IP protocol number 50. Firewalls don't always open these ports, so there's a possibility that IKEv2 VPN can't traverse proxies and firewalls.If I restart a client computer that I configured for point-to-site, will the VPN automatically reconnect?Automatic reconnection is a function of the client that you use. Windows supports automatic reconnection through the Always On VPN client feature.Does point-to-site support DDNS on the VPN clients?Dynamic DNS (DDNS) is currently not supported in point-to-site VPNs.Can site-to-site and point-to-site configurations coexist for the same virtual network?Yes. For the Resource Manager deployment model, you must have a route-based VPN type for your gateway. For the classic deployment model, you need a dynamic gateway. We don't support point-to-site for static routing VPN gateways or policy-based VPN gateways.Can I configure a point-to-site client to connect to multiple virtual network gateways at the same time?Depending on the VPN client software that you use, you might be able to connect to multiple virtual network gateways. But that's the case only if the virtual networks that you're connecting to don't have conflicting addressAWS Site-to-Site VPN quotas - AWS Site-to-Site VPN
Skip to main content This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. VPN Gateway FAQ Article02/18/2025 In this article -->This article answers frequently asked questions about Azure VPN Gateway cross-premises connections, hybrid configuration connections, and virtual network (VNet) gateways. It contains comprehensive information about point-to-site (P2S), site-to-site (S2S), and VNet-to-VNet configuration settings, including the Internet Protocol Security (IPsec) and Internet Key Exchange (IKE) protocols.Connecting to virtual networksCan I connect virtual networks in different Azure regions?Yes. There's no region constraint. One virtual network can connect to another virtual network in the same Azure region or in a different region.Can I connect virtual networks in different subscriptions?Yes.Can I specify private DNS servers in my VNet when configuring a VPN gateway?If you specify a Domain Name System (DNS) server or servers when you create your virtual network, the virtual private network (VPN) gateway uses those DNS servers. Verify that your specified DNS servers can resolve the domain names needed for Azure.Can I connect to multiple sites from a single virtual network?You can connect to multiple sites by using Windows PowerShell and the Azure REST APIs. See the Multi-site and VNet-to-VNet connectivity FAQ section.Is there an additional cost for setting up a VPN gateway as active-active?No. However, costs for any additional public IPs are charged accordingly. See IP address pricing.What are my cross-premises connection options?Azure VPN Gateway supports the following cross-premises gateway connections:Site-to-site: VPN connection over IPsec (IKEv1 and IKEv2). This type of connection requires a VPN device or Windows Server Routing and Remote Access. For more information, see Create a site-to-site VPN connection in the Azure portal.Point-to-site: VPN connection over Secure Socket Tunneling Protocol (SSTP) or IKEv2. This connection doesn't require a VPN device. For more information, see Configure server settings for point-to-site VPN Gateway certificate authentication.VNet-to-VNet: This type of connection is the same as a site-to-site configuration. VNet-to-VNet is a VPN connection over IPsec (IKEv1 and IKEv2). It doesn't require a VPN device. For more information, see Configure a VNet-to-VNet VPN gateway connection.Azure ExpressRoute: ExpressRoute is a private connection to Azure from your wide area network (WAN), not a VPN connection over the public internet. For more information, see the ExpressRoute technical overview and the ExpressRoute FAQ.For more information about VPN gateway connections, see What is Azure VPN Gateway?.What is the difference between site-to-site and point-to-site connections?Site-to-site (IPsec/IKE VPN tunnel) configurations are between your on-premises location and Azure. You can connect from any of your computers located on your premises to any virtual machine (VM) or role instance within your virtual network, depending on how you choose to configure routing and permissions. It's a great option for an always-available cross-premises connection and is well suited for hybrid configurations.This type of connection relies on an IPsec VPN appliance (hardware device or soft appliance). The appliance must be deployed at the edge of your network. To create this type of connection, you must have an externally facing IPv4 address.Point-to-site (VPN. FortiGate Site to Site VPN Configuration, FortiGate IPsec VPN Site to Site Configuration, How to Configure IPsec VPN Site to Site on FortiGate, ipsec vpn onVPN: Configuring Site to Site VPN using the
EIGRP MPLS VPN PE-CE Network TopologiesBenefits of the EIGRP MPLS VPN PE-CE Site of Origin Support FeatureEIGRP MPLS VPN PE-CE Site of Origin Support OverviewThe EIGRP MPLS VPN PE-CE Site of Origin feature introduces SoO support for EIGRP-to-BGP and BGP-to-EIGRP redistribution. The SoO extended community is a BGP extended community attribute that is used to identify routes that have originated from a site so that the readvertisement of that prefix back to the source site can be prevented. The SoO extended community uniquely identifies the site from which a PE router has learned a route. SoO support provides the capability to filter MPLS VPN traffic on a per-EIGRP-site basis. SoO filtering is configured at the interface level and is used to manage MPLS VPN traffic and to prevent routing loops from occurring in complex and mixed network topologies, such as EIGRP VPN sites that contain both VPN and backdoor links. The configuration of the SoO extended community allows MPLS VPN traffic to be filtered on a per-site basis. The SoO extended community is configured in an inbound BGP route map on the PE router and is applied to the interface. The SoO extended community can be applied to all exit points at the customer site for more specific filtering but must be configured on all interfaces of PE routers that provide VPN services to CE routers. Site of Origin Support for Backdoor LinksThe EIGRP MPLS VPN PE-CE Site of Origin (SoO) feature introduces support for backdoor links. A backdoor link or a route is a connection that is configured outside of the VPN between a remote and main site; for example, a WAN leased line that connects a remote site to the corporate network. Backdoor links are typically used as back up routes between EIGRP sites if the VPN link is down or not available. A metric is set on the backdoor link so that the route though the backdoor router is not selected unless there is a VPN link failure. The SoO extended community is defined on the interface of the backdoor router. It identifies the local site ID, which should match the value that is used on the PE routers that support the same site. When the backdoor router receives an EIGRP update (or reply) from a neighbor across the backdoor link, the router checks the update for an SoO value. If the SoO value in the EIGRP update matches the SoO value on the local backdoor interface, the route is rejected and not added to the EIGRP topology table. This scenario typically occurs when the route with the local SoO valued in the received EIGRP update was learned by the other VPN site and then advertised through the backdoor link by the backdoor router in the other VPN site. SoO filtering on the backdoor link prevents transient routing loops from occurring by filtering out EIGRP updates that contain routes that carry the local site ID. NoteIf a VPN site is partitioned and the SoO extended community attribute In policy-based VPNs, the Access rules determine which traffic is sent into the VPN tunnels. Types of tunnels in policy-based VPNs Policy-based VPNs can have two types of tunnels: IPsec tunnels — The IPsec protocol allows any IP traffic to be transported in the VPN regardless of which higher-level protocol the traffic uses on top of the IP protocol. Hosts can communicate through the VPN as if it was a normal link without the need for application-specific configurations on the gateway device. IPsec is part of both the IPv4 and IPv6 standards. IPsec is defined in RFC 4301. SSL VPN tunnels — SSL VPNs use secure sockets layer (SSL) encryption to provide secure remote access. With SSL VPNs, authenticated users establish secure connections to internal HTTP-based services through a web browser or through a client application. You can also use SSL VPN tunnels with the Stonesoft VPN Client in mobile VPNs. You can use SSL VPN tunnels alone, IPsec tunnels alone, or both SSL VPN and IPsec tunnels together in the same policy-based VPN. Site-to-site and mobile VPNs You can create VPNs between gateway devices or between a VPN client and a gateway device: A site-to-site VPN is created between two or more gateway devices that provide VPN access to several hosts in their internal networks. Site-to-site VPNs are supported for IPv4 and IPv6 traffic. A mobile VPN is created between a VPN client running on an individual computer and a gateway device. Mobile VPNs are supported only for IPv4 traffic. Figure: Site-to-site and mobile VPNs For mobile VPNs, we recommend using the Stonesoft VPN Client solution. Stonesoft VPN Client is available for the following platforms: Android (SSL VPN only) Mac OS (SSL VPN only) Windows (IPsec or SSL VPN) In mobile VPNs with IPsec tunnels, you can alternatively useClient-to-Site VPN vs. Site-to-Site VPN - This vs. That
If subnets are missed, HCX fails to form the service mesh.ImportantBy default, Azure assigns a private IP address from the GatewaySubnet prefix range automatically as the Azure BGP IP address on the Azure VPN gateway. The custom Azure APIPA BGP address is needed when your on premises VPN devices use an APIPA address (169.254.0.1 to 169.254.255.254) as the BGP IP. Azure VPN Gateway will choose the custom APIPA address if the corresponding local network gateway resource (on-premises network) has an APIPA address as the BGP peer IP. If the local network gateway uses a regular IP address (not APIPA), Azure VPN Gateway will revert to the private IP address from the GatewaySubnet range.Select Review + create.Navigate to the virtual hub you want, and deselect Hub association to connect your VPN site to the hub.(Optional) Create policy-based VPN site-to-site tunnelsImportantThis is an optional step and applies only to policy-based VPNs.Policy-based VPN setups require on-premises and Azure VMware Solution networks to be specified, including the hub ranges. These ranges specify the encryption domain of the policy-based VPN tunnel on-premises endpoint. The Azure VMware Solution side only requires the policy-based traffic selector indicator to be enabled.In the Azure portal, go to your Virtual WAN hub site and, under Connectivity, select VPN (Site to site).Select the VPN Site for which you want to set up a custom IPsec policy.Select your VPN site name, select More (...) at the far right, and then select Edit VPN Connection.Internet Protocol Security (IPsec), select Custom.Use policy-based traffic selector, select EnableSpecify the details for IKE Phase 1 and IKE Phase 2(ipsec).Change the IPsec setting from default to custom and customize the IPsec policy. Then select Save.Your traffic selectors or subnets that are part of the policy-based encryption domain should be:Virtual WAN hub /24Azure VMware Solution private cloud /22Connected Azure virtual network (if present)Connect your VPN site to the hubSelect your VPN site name and then select Connect VPN sites.In the Pre-shared key field, enter the key previously defined for the on-premises endpoint.TipIf you don't have a previously defined key, you can leave this field blank. A key is generated for you automatically.If you're deploying a firewall in the hub and it's the next hop, set the Propagate Default Route option to Enable.When enabled, the Virtual WAN hub propagates to a connection only if the hub already learned the default route when deploying a firewall in the hub or if another connected site forced tunneling enabled. The default route doesn't originate in the Virtual WAN hub.Select Connect. After a few minutes, the site shows the connection and connectivity status.Connection Status: Status of the Azure resource for the connection that connects the VPN site to the Azure hub’s VPN gateway. Once this control plane operation is successful, the Azure VPN gateway and the on-premises VPN device establish connectivity.Connectivity Status: Actual connectivity (data path) status between Azure’s VPN gateway in the hub and VPN site. It can show any of the following states:Unknown: Typically seen if the backend systems are working toGet started with AWS Site-to-Site VPN - AWS Site-to-Site VPN
Over SSTP) configurations let you connect from a single computer from anywhere to anything located in your virtual network. It uses the Windows built-in VPN client.As part of the point-to-site configuration, you install a certificate and a VPN client configuration package. The package contains the settings that allow your computer to connect to any virtual machine or role instance within the virtual network.This configuration is useful when you want to connect to a virtual network but aren't located on-premises. It's also a good option when you don't have access to VPN hardware or an externally facing IPv4 address, both of which are required for a site-to-site connection.You can configure your virtual network to use both site-to-site and point-to-site concurrently, as long as you create your site-to-site connection by using a route-based VPN type for your gateway. Route-based VPN types are called dynamic gateways in the classic deployment model.Does a misconfiguration of custom DNS break the normal operation of a VPN gateway?For normal functioning, the VPN gateway must establish a secure connection with the Azure control plane, facilitated through public IP addresses. This connection relies on resolving communication endpoints via public URLs. By default, Azure VNets use the built-in Azure DNS service (168.63.129.16) to resolve these public URLs. This default behavior helps ensure seamless communication between the VPN gateway and the Azure control plane.When you're implementing a custom DNS within a VNet, it's crucial to configure a DNS forwarder that points to Azure DNS (168.63.129.16). This configuration helps maintain uninterrupted communication between the VPN gateway and the control plane. Failure to set up a DNS forwarder to Azure DNS can prevent Microsoft from performing operations and maintenance on the VPN gateway, which poses a security risk.To help ensure proper functionality and healthy state for your VPN gateway, consider one of the following DNS configurations in the VNet:Revert to the Azure DNS default by removing the custom DNS within the VNet settings (recommended configuration).Add in your custom DNS configuration a DNS forwarder that points to Azure DNS (168.63.129.16). Depending on the specific rules and nature of your custom DNS, this setup might not resolve the issue as expected.Can two VPN clients connected in point-to-site to the same VPN gateway communicate?No. VPN clients connected in point-to-site to the same VPN gateway can't communicate with each other.When two VPN clients are connected to the same point-to-site VPN gateway, the gateway can automatically route traffic between them by determining the IP address that each client is assigned from the address pool. However, if the VPN clients are connected to different VPN gateways, routing between the VPN clients isn't possible because each VPN gateway is unaware of the IP address that the other gateway assigned to the client.Could a potential vulnerability known as "tunnel vision" affect point-to-site VPN connections?Microsoft is aware of reports about a network technique that bypasses VPN encapsulation. This is an industry-wide issue. It affects any operating system that implements a Dynamic Host Configuration Protocol (DHCP) client according to its RFC specification and. FortiGate Site to Site VPN Configuration, FortiGate IPsec VPN Site to Site Configuration, How to Configure IPsec VPN Site to Site on FortiGate, ipsec vpn onO que AWS Site-to-Site VPN? - AWS Site-to-Site VPN
VPN, short for Virtual Private Network, is a technology that allows secure communication over a public network. It works by utilizing security protocols like IPsec, IKEv2, PPTP, OpenVPN, WireGuard, and others to build tunnels between a client and a server. This tunnel encrypts online traffic and prevents third parties from eavesdropping. However, the initial applications of a VPN haven’t disappeared. One such implementation is the site to site VPN, whose advantages and disadvantages we will delve into in today’s article.Although invented back in the 90s to facilitate secure communication between the branches of a company, VPN has long since evolved into a comprehensive privacy and security tool. Due to the adaptation of commercial VPN providers, who aim to cultivate the online privacy and security sector to its full extent, VPNs have become more and more common. Nowadays, VPNs are best known for making remote access to the internet a possibility.What is a site to site VPN?A site to site VPN is a corporate implementation of the VPN technology. While most commercial VPN providers cater to the needs of a singular client, some offer this service. In broader terms, these kinds of VPNs are commercial Virtual Private Networks that can connect two locations, such as a public office to headquarters. This connection is secure as it encrypts any traffic between the two places. However, a site to site VPN can also create a web of interconnections between multiple areas, forming an integrated network.By location or area, we mean the exit point of a network. However, these networks aren’t interlinked. Instead, with site to site implementations, these systems, established in multiple locations, come together to form a unified but independent network. In a way, this VPN technology helps bridge the distance between real-world remote locations by creating a virtual and private networkComments
EIGRP MPLS VPN PE-CE Site of Origin The EIGRP MPLS VPN PE-CE Site of Origin feature introduces the capability to filter Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) traffic on a per-site basis for Enhanced Interior Gateway Routing Protocol (EIGRP) networks. Site of Origin (SoO) filtering is configured at the interface level and is used to manage MPLS VPN traffic and to prevent transient routing loops from occurring in complex and mixed network topologies. This feature is designed to support the MPLS VPN Support for EIGRP Between Provider Edge (PE) and Customer Edge (CE) feature. Support for backdoor links is provided by this feature when installed on PE routers that support EIGRP MPLS VPNs. Finding Feature InformationPrerequisites for EIGRP MPLS VPN PE-CE Site of OriginRestrictions for EIGRP MPLS VPN PE-CE Site of OriginInformation About EIGRP MPLS VPN PE-CE Site of OriginHow to Configure EIGRP MPLS VPN PE-CE Site of Origin SupportConfiguration Examples for EIGRP MPLS VPN PE-CE SoOAdditional ReferencesFeature Information for EIGRP MPLS VPN PE-CE Site of OriginGlossaryFinding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. Prerequisites for EIGRP MPLS VPN PE-CE Site of OriginThis document assumes that Border Gateway Protocol (BGP) is configured in the network core (or the service provider backbone). The following tasks will also need to be completed before you can configure this feature:This feature was introduced to support the MPLS VPN Support for EIGRP Between Provider Edge and Customer Edge feature and should be configured after the EIGRP MPLS VPN is created. All PE routers that are configured to support the EIGRP MPLS VPN must run Cisco IOS XE Release 2.1 or a later release, which provides support for the SoO extended community.Restrictions for EIGRP MPLS VPN PE-CE Site of OriginIf a VPN site is partitioned and the SoO extended community attribute is configured on a backdoor router interface, the backdoor link cannot be used as an alternate path to reach prefixes originated in other partitions of the same site. A unique SoO value must be configured for each individual VPN site. The same value must be configured on all provider edge and customer edge interfaces (if SoO is configured on the CE routers) that support the same VPN site. Information About EIGRP MPLS VPN PE-CE Site of OriginEIGRP MPLS VPN PE-CE Site of Origin Support OverviewSite of Origin Support for Backdoor LinksRouter Interoperation with the Site of Origin Extended CommunityRedistribution of BGP VPN Routes That Carry the Site of Origin into EIGRPBGP Cost Community Support for
2025-03-25When traffic is idle?This behavior is expected for policy-based (also known as static routing) VPN gateways. When the traffic over the tunnel is idle for more than five minutes, the tunnel is torn down. When traffic starts flowing in either direction, the tunnel is reestablished immediately.Can I use software VPNs to connect to Azure?We support Windows Server 2012 Routing and Remote Access servers for site-to-site cross-premises configuration.Other software VPN solutions should work with the gateway, as long as they conform to industry-standard IPsec implementations. For configuration and support instructions, contact the vendor of the software.Can I connect to a VPN gateway via point-to-site when located at a site that has an active site-to-site connection?Yes, but the public IP addresses of the point-to-site client must be different from the public IP addresses that the site-to-site VPN device uses, or else the point-to-site connection won't work. Point-to-site connections with IKEv2 can't be initiated from the same public IP addresses where a site-to-site VPN connection is configured on the same VPN gateway.Point-to-site connectionsHow many VPN client endpoints can I have in my point-to-site configuration?It depends on the gateway SKU. For more information on the supported number of connections, see Gateway SKUs.What client operating systems can I use with point-to-site?The following client operating systems are supported:Windows Server 2008 R2 (64-bit only)Windows 8.1 (32-bit and 64-bit)Windows Server 2012 (64-bit only)Windows Server 2012 R2 (64-bit only)Windows Server 2016 (64-bit only)Windows Server 2019 (64-bit only)Windows Server 2022 (64-bit only)Windows 10Windows 11macOS version 10.11 or laterLinux (strongSwan)iOSCan I traverse proxies and firewalls by using point-to-site capability?Azure supports three types of point-to-site VPN options:Secure Socket Tunneling Protocol (SSTP): A Microsoft proprietary SSL-based solution that can penetrate firewalls because most firewalls open the outbound TCP port that 443 SSL uses.OpenVPN: A SSL-based solution that can penetrate firewalls because most firewalls open the outbound TCP port that 443 SSL uses.IKEv2 VPN: A standards-based IPsec VPN solution that uses outbound UDP ports 500 and 4500, along with IP protocol number 50. Firewalls don't always open these ports, so there's a possibility that IKEv2 VPN can't traverse proxies and firewalls.If I restart a client computer that I configured for point-to-site, will the VPN automatically reconnect?Automatic reconnection is a function of the client that you use. Windows supports automatic reconnection through the Always On VPN client feature.Does point-to-site support DDNS on the VPN clients?Dynamic DNS (DDNS) is currently not supported in point-to-site VPNs.Can site-to-site and point-to-site configurations coexist for the same virtual network?Yes. For the Resource Manager deployment model, you must have a route-based VPN type for your gateway. For the classic deployment model, you need a dynamic gateway. We don't support point-to-site for static routing VPN gateways or policy-based VPN gateways.Can I configure a point-to-site client to connect to multiple virtual network gateways at the same time?Depending on the VPN client software that you use, you might be able to connect to multiple virtual network gateways. But that's the case only if the virtual networks that you're connecting to don't have conflicting address
2025-03-30Skip to main content This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. VPN Gateway FAQ Article02/18/2025 In this article -->This article answers frequently asked questions about Azure VPN Gateway cross-premises connections, hybrid configuration connections, and virtual network (VNet) gateways. It contains comprehensive information about point-to-site (P2S), site-to-site (S2S), and VNet-to-VNet configuration settings, including the Internet Protocol Security (IPsec) and Internet Key Exchange (IKE) protocols.Connecting to virtual networksCan I connect virtual networks in different Azure regions?Yes. There's no region constraint. One virtual network can connect to another virtual network in the same Azure region or in a different region.Can I connect virtual networks in different subscriptions?Yes.Can I specify private DNS servers in my VNet when configuring a VPN gateway?If you specify a Domain Name System (DNS) server or servers when you create your virtual network, the virtual private network (VPN) gateway uses those DNS servers. Verify that your specified DNS servers can resolve the domain names needed for Azure.Can I connect to multiple sites from a single virtual network?You can connect to multiple sites by using Windows PowerShell and the Azure REST APIs. See the Multi-site and VNet-to-VNet connectivity FAQ section.Is there an additional cost for setting up a VPN gateway as active-active?No. However, costs for any additional public IPs are charged accordingly. See IP address pricing.What are my cross-premises connection options?Azure VPN Gateway supports the following cross-premises gateway connections:Site-to-site: VPN connection over IPsec (IKEv1 and IKEv2). This type of connection requires a VPN device or Windows Server Routing and Remote Access. For more information, see Create a site-to-site VPN connection in the Azure portal.Point-to-site: VPN connection over Secure Socket Tunneling Protocol (SSTP) or IKEv2. This connection doesn't require a VPN device. For more information, see Configure server settings for point-to-site VPN Gateway certificate authentication.VNet-to-VNet: This type of connection is the same as a site-to-site configuration. VNet-to-VNet is a VPN connection over IPsec (IKEv1 and IKEv2). It doesn't require a VPN device. For more information, see Configure a VNet-to-VNet VPN gateway connection.Azure ExpressRoute: ExpressRoute is a private connection to Azure from your wide area network (WAN), not a VPN connection over the public internet. For more information, see the ExpressRoute technical overview and the ExpressRoute FAQ.For more information about VPN gateway connections, see What is Azure VPN Gateway?.What is the difference between site-to-site and point-to-site connections?Site-to-site (IPsec/IKE VPN tunnel) configurations are between your on-premises location and Azure. You can connect from any of your computers located on your premises to any virtual machine (VM) or role instance within your virtual network, depending on how you choose to configure routing and permissions. It's a great option for an always-available cross-premises connection and is well suited for hybrid configurations.This type of connection relies on an IPsec VPN appliance (hardware device or soft appliance). The appliance must be deployed at the edge of your network. To create this type of connection, you must have an externally facing IPv4 address.Point-to-site (VPN
2025-04-16EIGRP MPLS VPN PE-CE Network TopologiesBenefits of the EIGRP MPLS VPN PE-CE Site of Origin Support FeatureEIGRP MPLS VPN PE-CE Site of Origin Support OverviewThe EIGRP MPLS VPN PE-CE Site of Origin feature introduces SoO support for EIGRP-to-BGP and BGP-to-EIGRP redistribution. The SoO extended community is a BGP extended community attribute that is used to identify routes that have originated from a site so that the readvertisement of that prefix back to the source site can be prevented. The SoO extended community uniquely identifies the site from which a PE router has learned a route. SoO support provides the capability to filter MPLS VPN traffic on a per-EIGRP-site basis. SoO filtering is configured at the interface level and is used to manage MPLS VPN traffic and to prevent routing loops from occurring in complex and mixed network topologies, such as EIGRP VPN sites that contain both VPN and backdoor links. The configuration of the SoO extended community allows MPLS VPN traffic to be filtered on a per-site basis. The SoO extended community is configured in an inbound BGP route map on the PE router and is applied to the interface. The SoO extended community can be applied to all exit points at the customer site for more specific filtering but must be configured on all interfaces of PE routers that provide VPN services to CE routers. Site of Origin Support for Backdoor LinksThe EIGRP MPLS VPN PE-CE Site of Origin (SoO) feature introduces support for backdoor links. A backdoor link or a route is a connection that is configured outside of the VPN between a remote and main site; for example, a WAN leased line that connects a remote site to the corporate network. Backdoor links are typically used as back up routes between EIGRP sites if the VPN link is down or not available. A metric is set on the backdoor link so that the route though the backdoor router is not selected unless there is a VPN link failure. The SoO extended community is defined on the interface of the backdoor router. It identifies the local site ID, which should match the value that is used on the PE routers that support the same site. When the backdoor router receives an EIGRP update (or reply) from a neighbor across the backdoor link, the router checks the update for an SoO value. If the SoO value in the EIGRP update matches the SoO value on the local backdoor interface, the route is rejected and not added to the EIGRP topology table. This scenario typically occurs when the route with the local SoO valued in the received EIGRP update was learned by the other VPN site and then advertised through the backdoor link by the backdoor router in the other VPN site. SoO filtering on the backdoor link prevents transient routing loops from occurring by filtering out EIGRP updates that contain routes that carry the local site ID. NoteIf a VPN site is partitioned and the SoO extended community attribute
2025-04-09