Tink 2 or 3
Author: c | 2025-04-24
2 or 3 lyrics, 2 or 3, Tink, Tink lyrics, Song lyrics. search menu. search Charts Genres. Add Song. LyricFind. 2 or 3. Hopeless Romantic
Tink - 2 Or 3 Lyrics
Import com.google.crypto.tink.aead.PredefinedAeadParameters; // 1. Generate the key material. KeysetHandle keysetHandle = KeysetHandle.generateNew( PredefinedAeadParameters.AES128_GCM); // 2. Get the primitive. Aead aead = keysetHandle.getPrimitive(Aead.class); // 3. Use the primitive to encrypt a plaintext, byte[] ciphertext = aead.encrypt(plaintext, aad); // ... or to decrypt a ciphertext. byte[] decrypted = aead.decrypt(ciphertext, aad);Deterministic symmetric key encryptionYou can obtain and use a DeterministicAEAD (Deterministic Authenticated Encryption with Associated Data primitive to encrypt or decrypt data: import com.google.crypto.tink.daead.PredefinedDeterministicAeadParameters; import com.google.crypto.tink.KeysetHandle; // 1. Generate the key material. KeysetHandle keysetHandle = KeysetHandle.generateNew( PredefinedDeterministicAeadParameters.AES256_SIV); // 2. Get the primitive. DeterministicAead daead = keysetHandle.getPrimitive(DeterministicAead.class); // 3. Use the primitive to deterministically encrypt a plaintext, byte[] ciphertext = daead.encryptDeterministically(plaintext, aad); // ... or to deterministically decrypt a ciphertext. byte[] decrypted = daead.decryptDeterministically(ciphertext, aad);Symmetric key encryption of streaming dataSee Authentication CodeSee signaturesSee encryptionSee encryptionVia the AEAD interface, Tink supports envelope encryption.For example, you can perform envelope encryption with a Google Cloud KMS key at gcp-kms://projects/tink-examples/locations/global/keyRings/foo/cryptoKeys/bar using the credentials in credentials.json as follows: import com.google.crypto.tink.Aead; import com.google.crypto.tink.KeyTemplates; import com.google.crypto.tink.KeysetHandle; import com.google.crypto.tink.KmsClients; import com.google.crypto.tink.aead.KmsEnvelopeAeadKeyManager; import com.google.crypto.tink.integration.gcpkms.GcpKmsClient; // 1. Generate the key material. String kmsKeyUri = "gcp-kms://projects/tink-examples/locations/global/keyRings/foo/cryptoKeys/bar"; KeysetHandle handle = KeysetHandle.generateNew( KmsEnvelopeAeadKeyManager.createKeyTemplate( kmsKeyUri, KeyTemplates.get("AES128_GCM"))); // 2. Register the KMS client. KmsClients.add(new GcpKmsClient() .withCredentials("credentials.json")); // 3. Get the primitive. Aead aead = handle.getPrimitive(Aead.class); // 4. Use the primitive. byte[] ciphertext = aead.encrypt(plaintext, aad);Key rotationSupport for key rotation in Tink is provided via the KeysetHandle.Builder class.You have to provide a KeysetHandle-object that contains the keyset that should be rotated, and a specification of the new key via a
Stream 2 or 3 by Tink
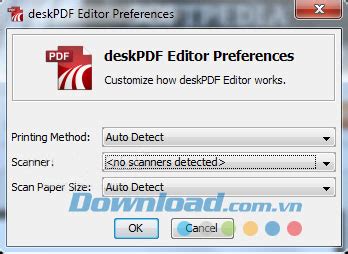
The following examples show how to create a keyset with a single key andstore it in plaintext on disk.Tinkeytinkey create-keyset \ --key-template AES128_GCM \ --out-format json \ --out aead_keyset.jsonJavapackage cleartextkeyset;import static java.nio.charset.StandardCharsets.UTF_8;import com.google.crypto.tink.Aead;import com.google.crypto.tink.InsecureSecretKeyAccess;import com.google.crypto.tink.KeysetHandle;import com.google.crypto.tink.RegistryConfiguration;import com.google.crypto.tink.TinkJsonProtoKeysetFormat;import com.google.crypto.tink.aead.AeadConfig;import com.google.crypto.tink.aead.PredefinedAeadParameters;import java.nio.file.Files;import java.nio.file.Path;import java.nio.file.Paths;/** * A command-line utility for generating, storing and using AES128_GCM keysets. * * WARNING: Loading a Keyset from disk is often a security problem -- hence this needs {@code * InsecureSecretKeyAccess.get()}. * * It requires the following arguments: * * * mode: Can be "generate", "encrypt" or "decrypt". If mode is "generate" it will generate, * encrypt a keyset, store it in key-file. If mode is "encrypt" or "decrypt" it will read and * decrypt an keyset from key-file, and use it to encrypt or decrypt input-file. * key-file: Read the encrypted key material from this file. * input-file: If mode is "encrypt" or "decrypt", read the input from this file. * output-file: If mode is "encrypt" or "decrypt", write the result to this file. */public final class CleartextKeysetExample { private static final String MODE_ENCRYPT = "encrypt"; private static final String MODE_DECRYPT = "decrypt"; private static final String MODE_GENERATE = "generate"; private static final byte[] EMPTY_ASSOCIATED_DATA = new byte[0]; public static void main(String[] args) throws Exception { if (args.length != 2 && args.length != 4) { System.err.printf("Expected 2 or 4 parameters, got %d\n", args.length); System.err.println( "Usage: java CleartextKeysetExample generate/encrypt/decrypt key-file input-file" + " output-file"); System.exit(1); } String mode = args[0]; if (!MODE_ENCRYPT.equals(mode) && !MODE_DECRYPT.equals(mode) && !MODE_GENERATE.equals(mode)) { System.err.print("The first argument should be either encrypt, decrypt or generate"); System.exit(1); } Path keyFile = Paths.get(args[1]); // Initialise Tink: register all AEAD key types with the Tink runtime AeadConfig.register(); if (MODE_GENERATE.equals(mode)) { KeysetHandle handle = KeysetHandle.generateNew(PredefinedAeadParameters.AES128_GCM); String serializedKeyset = TinkJsonProtoKeysetFormat.serializeKeyset(handle, InsecureSecretKeyAccess.get()); Files.write(keyFile, serializedKeyset.getBytes(UTF_8)); return; } // Use the primitive to encrypt/decrypt files // Read the keyset from disk String serializedKeyset = new String(Files.readAllBytes(keyFile), UTF_8); KeysetHandle handle = TinkJsonProtoKeysetFormat.parseKeyset(serializedKeyset, InsecureSecretKeyAccess.get()); // Get the primitive Aead aead = handle.getPrimitive(RegistryConfiguration.get(), Aead.class); byte[] input = Files.readAllBytes(Paths.get(args[2])); Path outputFile = Paths.get(args[3]); if (MODE_ENCRYPT.equals(mode)) { byte[] ciphertext = aead.encrypt(input, EMPTY_ASSOCIATED_DATA); Files.write(outputFile, ciphertext); } else if (MODE_DECRYPT.equals(mode)) { byte[] plaintext = aead.decrypt(input, EMPTY_ASSOCIATED_DATA); Files.write(outputFile, plaintext); } } private CleartextKeysetExample() {}}Goimport ( "bytes" "fmt" "log" "github.com/tink-crypto/tink-go/v2/aead" "github.com/tink-crypto/tink-go/v2/insecurecleartextkeyset" "github.com/tink-crypto/tink-go/v2/keyset")func Example_cleartextKeysetInBinary() { // Generate a new keyset handle for the primitive we want to use. handle, err := keyset.NewHandle(aead.AES256GCMKeyTemplate()) if err != nil { log.Fatal(err) } // Serialize the keyset. buff := &bytes.Buffer{} err = insecurecleartextkeyset.Write(handle, keyset.NewBinaryWriter(buff)) if err != nil { log.Fatal(err) } serializedKeyset := buff.Bytes() // serializedKeyset can now be stored at a secure location. // WARNING: Storing the keyset in cleartext to disk is not recommended! // Parse the keyset. parsedHandle, err := insecurecleartextkeyset.Read( keyset.NewBinaryReader(bytes.NewBuffer(serializedKeyset))) if err != nil { log.Fatal(err) } // Get the primitive. primitive, err := aead.New(parsedHandle) if err != nil { log.Fatal(err) } // Use the primitive. plaintext := []byte("message") associatedData := []byte("example encryption") ciphertext, err := primitive.Encrypt(plaintext, associatedData) if err != nil { log.Fatal(err) } decrypted, err := primitive.Decrypt(ciphertext, associatedData) if err !=2 OR 3 Lyrics - TINK
Parameters object. import com.google.crypto.tink.KeysetHandle; import com.google.crypto.tink.KeysetManager; KeysetHandle keysetHandle = ...; // existing keyset KeysetHandle.Builder builder = KeysetHandle.newBuilder(keysetHandle); builder.addEntry(KeysetHandle.generateEntryFromParameters( ChaCha20Poly1305Parameters.create()).withRandomId()); KeysetHandle keysetHandleWithAdditionalEntry = builder.build();After a successful rotation, the resulting keyset contains a new key generated according to the specification in the parameters object. For the rotation to succeed the Registry must contain a key manager for the key type specified in keyTemplate.Alternatively, you can use Tinkey to rotate or manage a keyset.Custom implementation of a primitiveNOTE: The usage of custom key managers should be enjoyed responsibly. We (i.e. Tink developers) have no way of checking or enforcing that a custom implementation satisfies security properties of the corresponding primitive interface, so it is up to the implementer and the user of the custom implementation ensure the required properties are met.The main cryptographic operations offered by Tink are accessible via so-called primitives, which are interfaces that represent corresponding cryptographic functionalities. While Tink comes with several standard implementations of common primitives, it also allows for adding custom implementations of primitives. Such implementations allow for seamless integration of Tink with custom third-party cryptographic schemes or hardware modules, and in combination with key rotation features, enables the painless migration between cryptographic schemes.To create a custom implementation of a primitive proceed as follows:Determine for which primitive a custom implementation is needed.Define protocol buffers that hold key material and parameters for the custom cryptographic scheme; the name of the key protocol buffer (a.k.a. type URL) determines the key type for the custom implementation.Implement a KeyManager interface for the. 2 or 3 lyrics, 2 or 3, Tink, Tink lyrics, Song lyrics. search menu. search Charts Genres. Add Song. LyricFind. 2 or 3. Hopeless RomanticTink - 2 or 3 Lyrics
“Lala”-Lala in teletubbies and slendytubbies theme animationsAppearance[]lala is a yellow furred Teletubby with a swoop as her antenna.Appearances[]tinky winky x po[]Lala gets infuriated after hearing that Shadow tubby has kidnapped po, they also explore the cave.Slendytubbies[]She’s a central character as she once had a bad dream and was also not very happy when she got the custard, But at night, after Tinky Winky goes out to a forest, she goes with Po but they both end up killed.After being killed, Lala is in the ruins where White tubby crushes her after he collects all the custards.Naa naa’s life 2[]They appear near the end when James is killed and everyone celebratesNaa naa’s life 3[]They are seen hugging Naa Naa after hearing the news that she is pregnantTink tink’s life story remake[]She is introduced to tink tink, and when Naa naa and tink tink are captured, she decides to help with Dipsy.Layla’s life[]She gets introduced yet again and does many other things like: seeing po tickle tinky, get afraid when the bush is moving, and that’s it, they also help Layla and cici get outThe reunion[]like the others, she’s a main character that both stops the newborns and noo noo.Stenfany’s life[]she does the same as Layla’s life, except for seeing po tickle tinky winky, oh yeah and she throws one of Haley’s friends into the air.Arlind’s life[]they do the same as both stenfany, and Layla’s life, except for seeing po tickle tinky and be afraid when the bush is moving.Trivia[]lala’s antenna is just an add on for Dipsy’s antennaNo one knows how to actually spell her name, so they either choose laa laa or lala.Knxwledge's '2-3' sample of Tink's '2 or 3'
OUR FAVORITES Let’s Play Monopoly! MONOPOLY: The Board Game Roll the Dice, Pass Go & Win View Breaking out the Monopoly board has been a family tradition for decades. Also part of the tradition: not finishing the game because you’ve run out of time! There’s another way. With brilliant tweaks that keep things fast, fun, and authentic, Monopoly on the App Store is a winning investment. Here are five reasons to rediscover your inner tycoon with this superslick mobile version. Roll the dice, scoop up property, and own the town. 1. It’s easy! Whether you start a pass-and-play game with friends in the same room or compete online, setup is a breeze. Select your rules, fight over who gets the top hat token, and you’re off. And no more designated banker duties: Finances are handled automatically, leaving you to focus on wheeling, dealing, and bankrupting others. 2. It’s quick! Can’t wrap up a game in one sitting? Just pause and come back later. Or better yet, play a zippier version of the game with rules that seriously speed things up, like cheaper hotels and no taxes. Your accountant will need to find another gig! 3. It’s customizable! Monopoly’s rules have barely changed since 1935—so why not tweak the rule book? Collect $400 (instead of $200) for landing directly on Go. Or get out of jail after just one turn. It’s your call! Welcome to Transylvania! Beware the fog. 4. It’s beautiful! The digital version has real flair. Animated tokens merrily tink-tink-tink past properties. Little trains chug along, while tiny helicopters dot the sky. There’s even a police siren when you get hauled off to jail. 5. It’s expandable! Tired of the same sights? Fun add-ons let you try new tokens and themes, like a snowswept ski resort or the lovelyTink – 2 or 3 Lyrics - Genius
Visa has announced plans to acquire Tink for €1.8 billion, or $2.15 billion at today’s exchange rate. Tink has been a leading fintech startup in Europe focused on open banking application programming interfaces (APIs).Today’s move comes a few months after Visa abandoned its acquisition of Plaid, another popular open banking startup. Originally, Visa planned to spend $5.3 billion to acquire the American startup. But the company had to call off the acquisition after running into a regulatory wall.Tink offers a single API so that customers can connect to bank accounts from their own apps and services. For instance, you can leverage Tink’s API to access account statements, initiate payments, fetch banking information and refresh this data regularly.While banks and financial institutions now all have to offer open banking interfaces due to the EU’s Payment Services Directive PSD2, there’s no single standard. Tink integrates with 3,400 banks and financial institutions.App developers can use the same API call to interact with bank accounts across various financial institutions. As you may have guessed, it greatly simplifies the adoption of open banking features.300 banks and fintech startups use Tink’s API to access third-party bank information — clients include PayPal, BNP Paribas, American Express and Lydia. Overall, Tink covers 250 million bank customers across Europe.Based in Stockholm, Sweden, Tink operations should continue as usual after the acquisition. Visa plans to retain the brand and management team.According to Crunchbase data, Tink has raised over $300 million from Dawn Capital, Eurazeo, HMI Capital, Insight Partners, PayPal Ventures,. 2 or 3 lyrics, 2 or 3, Tink, Tink lyrics, Song lyrics. search menu. search Charts Genres. Add Song. LyricFind. 2 or 3. Hopeless Romantic Tink 2 Or 3 Lyrics. 2 Or 3 lyrics performed by Tink: Brightboy Okay, okay Honorary Members See I'm young and I'mComments
Import com.google.crypto.tink.aead.PredefinedAeadParameters; // 1. Generate the key material. KeysetHandle keysetHandle = KeysetHandle.generateNew( PredefinedAeadParameters.AES128_GCM); // 2. Get the primitive. Aead aead = keysetHandle.getPrimitive(Aead.class); // 3. Use the primitive to encrypt a plaintext, byte[] ciphertext = aead.encrypt(plaintext, aad); // ... or to decrypt a ciphertext. byte[] decrypted = aead.decrypt(ciphertext, aad);Deterministic symmetric key encryptionYou can obtain and use a DeterministicAEAD (Deterministic Authenticated Encryption with Associated Data primitive to encrypt or decrypt data: import com.google.crypto.tink.daead.PredefinedDeterministicAeadParameters; import com.google.crypto.tink.KeysetHandle; // 1. Generate the key material. KeysetHandle keysetHandle = KeysetHandle.generateNew( PredefinedDeterministicAeadParameters.AES256_SIV); // 2. Get the primitive. DeterministicAead daead = keysetHandle.getPrimitive(DeterministicAead.class); // 3. Use the primitive to deterministically encrypt a plaintext, byte[] ciphertext = daead.encryptDeterministically(plaintext, aad); // ... or to deterministically decrypt a ciphertext. byte[] decrypted = daead.decryptDeterministically(ciphertext, aad);Symmetric key encryption of streaming dataSee Authentication CodeSee signaturesSee encryptionSee encryptionVia the AEAD interface, Tink supports envelope encryption.For example, you can perform envelope encryption with a Google Cloud KMS key at gcp-kms://projects/tink-examples/locations/global/keyRings/foo/cryptoKeys/bar using the credentials in credentials.json as follows: import com.google.crypto.tink.Aead; import com.google.crypto.tink.KeyTemplates; import com.google.crypto.tink.KeysetHandle; import com.google.crypto.tink.KmsClients; import com.google.crypto.tink.aead.KmsEnvelopeAeadKeyManager; import com.google.crypto.tink.integration.gcpkms.GcpKmsClient; // 1. Generate the key material. String kmsKeyUri = "gcp-kms://projects/tink-examples/locations/global/keyRings/foo/cryptoKeys/bar"; KeysetHandle handle = KeysetHandle.generateNew( KmsEnvelopeAeadKeyManager.createKeyTemplate( kmsKeyUri, KeyTemplates.get("AES128_GCM"))); // 2. Register the KMS client. KmsClients.add(new GcpKmsClient() .withCredentials("credentials.json")); // 3. Get the primitive. Aead aead = handle.getPrimitive(Aead.class); // 4. Use the primitive. byte[] ciphertext = aead.encrypt(plaintext, aad);Key rotationSupport for key rotation in Tink is provided via the KeysetHandle.Builder class.You have to provide a KeysetHandle-object that contains the keyset that should be rotated, and a specification of the new key via a
2025-04-02The following examples show how to create a keyset with a single key andstore it in plaintext on disk.Tinkeytinkey create-keyset \ --key-template AES128_GCM \ --out-format json \ --out aead_keyset.jsonJavapackage cleartextkeyset;import static java.nio.charset.StandardCharsets.UTF_8;import com.google.crypto.tink.Aead;import com.google.crypto.tink.InsecureSecretKeyAccess;import com.google.crypto.tink.KeysetHandle;import com.google.crypto.tink.RegistryConfiguration;import com.google.crypto.tink.TinkJsonProtoKeysetFormat;import com.google.crypto.tink.aead.AeadConfig;import com.google.crypto.tink.aead.PredefinedAeadParameters;import java.nio.file.Files;import java.nio.file.Path;import java.nio.file.Paths;/** * A command-line utility for generating, storing and using AES128_GCM keysets. * * WARNING: Loading a Keyset from disk is often a security problem -- hence this needs {@code * InsecureSecretKeyAccess.get()}. * * It requires the following arguments: * * * mode: Can be "generate", "encrypt" or "decrypt". If mode is "generate" it will generate, * encrypt a keyset, store it in key-file. If mode is "encrypt" or "decrypt" it will read and * decrypt an keyset from key-file, and use it to encrypt or decrypt input-file. * key-file: Read the encrypted key material from this file. * input-file: If mode is "encrypt" or "decrypt", read the input from this file. * output-file: If mode is "encrypt" or "decrypt", write the result to this file. */public final class CleartextKeysetExample { private static final String MODE_ENCRYPT = "encrypt"; private static final String MODE_DECRYPT = "decrypt"; private static final String MODE_GENERATE = "generate"; private static final byte[] EMPTY_ASSOCIATED_DATA = new byte[0]; public static void main(String[] args) throws Exception { if (args.length != 2 && args.length != 4) { System.err.printf("Expected 2 or 4 parameters, got %d\n", args.length); System.err.println( "Usage: java CleartextKeysetExample generate/encrypt/decrypt key-file input-file" + " output-file"); System.exit(1); } String mode = args[0]; if (!MODE_ENCRYPT.equals(mode) && !MODE_DECRYPT.equals(mode) && !MODE_GENERATE.equals(mode)) { System.err.print("The first argument should be either encrypt, decrypt or generate"); System.exit(1); } Path keyFile = Paths.get(args[1]); // Initialise Tink: register all AEAD key types with the Tink runtime AeadConfig.register(); if (MODE_GENERATE.equals(mode)) { KeysetHandle handle = KeysetHandle.generateNew(PredefinedAeadParameters.AES128_GCM); String serializedKeyset = TinkJsonProtoKeysetFormat.serializeKeyset(handle, InsecureSecretKeyAccess.get()); Files.write(keyFile, serializedKeyset.getBytes(UTF_8)); return; } // Use the primitive to encrypt/decrypt files // Read the keyset from disk String serializedKeyset = new String(Files.readAllBytes(keyFile), UTF_8); KeysetHandle handle = TinkJsonProtoKeysetFormat.parseKeyset(serializedKeyset, InsecureSecretKeyAccess.get()); // Get the primitive Aead aead = handle.getPrimitive(RegistryConfiguration.get(), Aead.class); byte[] input = Files.readAllBytes(Paths.get(args[2])); Path outputFile = Paths.get(args[3]); if (MODE_ENCRYPT.equals(mode)) { byte[] ciphertext = aead.encrypt(input, EMPTY_ASSOCIATED_DATA); Files.write(outputFile, ciphertext); } else if (MODE_DECRYPT.equals(mode)) { byte[] plaintext = aead.decrypt(input, EMPTY_ASSOCIATED_DATA); Files.write(outputFile, plaintext); } } private CleartextKeysetExample() {}}Goimport ( "bytes" "fmt" "log" "github.com/tink-crypto/tink-go/v2/aead" "github.com/tink-crypto/tink-go/v2/insecurecleartextkeyset" "github.com/tink-crypto/tink-go/v2/keyset")func Example_cleartextKeysetInBinary() { // Generate a new keyset handle for the primitive we want to use. handle, err := keyset.NewHandle(aead.AES256GCMKeyTemplate()) if err != nil { log.Fatal(err) } // Serialize the keyset. buff := &bytes.Buffer{} err = insecurecleartextkeyset.Write(handle, keyset.NewBinaryWriter(buff)) if err != nil { log.Fatal(err) } serializedKeyset := buff.Bytes() // serializedKeyset can now be stored at a secure location. // WARNING: Storing the keyset in cleartext to disk is not recommended! // Parse the keyset. parsedHandle, err := insecurecleartextkeyset.Read( keyset.NewBinaryReader(bytes.NewBuffer(serializedKeyset))) if err != nil { log.Fatal(err) } // Get the primitive. primitive, err := aead.New(parsedHandle) if err != nil { log.Fatal(err) } // Use the primitive. plaintext := []byte("message") associatedData := []byte("example encryption") ciphertext, err := primitive.Encrypt(plaintext, associatedData) if err != nil { log.Fatal(err) } decrypted, err := primitive.Decrypt(ciphertext, associatedData) if err !=
2025-04-15“Lala”-Lala in teletubbies and slendytubbies theme animationsAppearance[]lala is a yellow furred Teletubby with a swoop as her antenna.Appearances[]tinky winky x po[]Lala gets infuriated after hearing that Shadow tubby has kidnapped po, they also explore the cave.Slendytubbies[]She’s a central character as she once had a bad dream and was also not very happy when she got the custard, But at night, after Tinky Winky goes out to a forest, she goes with Po but they both end up killed.After being killed, Lala is in the ruins where White tubby crushes her after he collects all the custards.Naa naa’s life 2[]They appear near the end when James is killed and everyone celebratesNaa naa’s life 3[]They are seen hugging Naa Naa after hearing the news that she is pregnantTink tink’s life story remake[]She is introduced to tink tink, and when Naa naa and tink tink are captured, she decides to help with Dipsy.Layla’s life[]She gets introduced yet again and does many other things like: seeing po tickle tinky, get afraid when the bush is moving, and that’s it, they also help Layla and cici get outThe reunion[]like the others, she’s a main character that both stops the newborns and noo noo.Stenfany’s life[]she does the same as Layla’s life, except for seeing po tickle tinky winky, oh yeah and she throws one of Haley’s friends into the air.Arlind’s life[]they do the same as both stenfany, and Layla’s life, except for seeing po tickle tinky and be afraid when the bush is moving.Trivia[]lala’s antenna is just an add on for Dipsy’s antennaNo one knows how to actually spell her name, so they either choose laa laa or lala.
2025-03-26OUR FAVORITES Let’s Play Monopoly! MONOPOLY: The Board Game Roll the Dice, Pass Go & Win View Breaking out the Monopoly board has been a family tradition for decades. Also part of the tradition: not finishing the game because you’ve run out of time! There’s another way. With brilliant tweaks that keep things fast, fun, and authentic, Monopoly on the App Store is a winning investment. Here are five reasons to rediscover your inner tycoon with this superslick mobile version. Roll the dice, scoop up property, and own the town. 1. It’s easy! Whether you start a pass-and-play game with friends in the same room or compete online, setup is a breeze. Select your rules, fight over who gets the top hat token, and you’re off. And no more designated banker duties: Finances are handled automatically, leaving you to focus on wheeling, dealing, and bankrupting others. 2. It’s quick! Can’t wrap up a game in one sitting? Just pause and come back later. Or better yet, play a zippier version of the game with rules that seriously speed things up, like cheaper hotels and no taxes. Your accountant will need to find another gig! 3. It’s customizable! Monopoly’s rules have barely changed since 1935—so why not tweak the rule book? Collect $400 (instead of $200) for landing directly on Go. Or get out of jail after just one turn. It’s your call! Welcome to Transylvania! Beware the fog. 4. It’s beautiful! The digital version has real flair. Animated tokens merrily tink-tink-tink past properties. Little trains chug along, while tiny helicopters dot the sky. There’s even a police siren when you get hauled off to jail. 5. It’s expandable! Tired of the same sights? Fun add-ons let you try new tokens and themes, like a snowswept ski resort or the lovely
2025-04-10[Intro: Yung Bleu & Tink](Hitmaka)I told youStingyYeah[Pre-Chorus: Tink]How many times, did you tell me that you love me but you lied? (You lied)What could I do (I do), to make you love me like the way you're supposed to doDon't want nobody in my bed, only you (Only you)[Chorus: Tink & Yung Bleu, Yung Bleu]I'm so stingy with your loveI'm so stingy with your loveShe just like my favorite drugStingy with your loveYou got me bein' stingy with your loveDon't want nobody else to feel your touchDon't want nobody else to feel your touch(I'm so stingy)[Verse 1: Yung Bleu]Posin' like a '64 (Posin' like a '64)Type of shit that get you sent for (Type of shit that get you sent for)I'm on the way, girl, send your info (Send your info)I got her fuckin' like a nympho (Like a nympho, baby)I don't want nobody to be touchin' on your bodyDon't move on, I'm undecidedDon't move on, I'm undecided[Pre-Chorus: Yung Bleu & Tink]How many times, did you tell me you'll stay down but you lied? (But you lied)What could it be? Is it love that came and took control of meCan't have nobody in your bed, only me (Only you)[Chorus: Tink & Yung Bleu, Yung Bleu]I'm so stingy with your loveI'm so stingy with your loveShe just like my favorite drugStingy with your loveYou got me bein' stingy with your loveDon't want nobody else to feel your touchDon't want nobody else to feel your touch(I'm so stingy)[Verse 2: Tink]Throw it like a pitchKill it like a thirty round clipShow me how to loveFuck a hunnid rounds then lay in it when you're doneSay you'll never leave, every minute that I'm with youHoldin' onto me even though we ain't officialI'm the only one that really get youTell me everything you done been throughI don't wanna lose you to no one else (Lose you to no one else)I don't feel the same when I'm by myselfYou got me bein' stingy, can't let nobody near youStarin' in my eyes like you lookin' through a mirrorI give you my soul, have you feelin' like a
2025-03-30