Routing and remote access services
Author: m | 2025-04-24

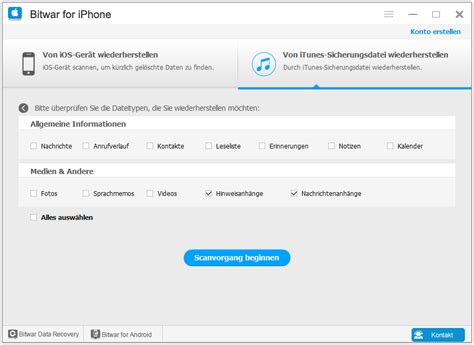
To resolve this behavior, stop the Routing and Remote Access service, start Remote Registry service, and then restart the Routing and Remote Access service. To do this To fix the routing and remote access service not starting. I have to restart the 'network policy server' service. Then start the 'routing and remote access' service. Routing and
Routing and Remote Access Service (Remote Access)
Not for the sha256 Thumbprint algorithm. If there is mismtach between the hash of the certificate on the remote access server and the Web proxy server, right-click the certificate on the remote access server, and then click Delete . Remove the certificate binding from HTTPS Listener. Type the following commands in a command window: netsh http delete sslcert ipport=0.0.0.0:443 netsh http delete sslcert ipport=[::]:443 Remove the certificate binding in the Routing and Remote Access service. Open the Registry Editor and delete the following registry keys (if present): HKLM\System\CurrentControlSet\Services\Sstpsvc\Parameters\Sha256CertificateHash HKLM\System\CurrentControlSet\Services\Sstpsvc\Parameters\Sha1CertificateHash Add the new certificate inside the certificate store (local computer store). Plumb the new certificate to the HTTPS Listener (assuming the new certificate has SHA1 certificate hash as xxx). Type the following commands in a command window: netsh http add sslcert ipport=0.0.0.0:443 certhash= appid={ba195980-cd49-458b-9e23-c84ee0adcd75} certstorename=MY netsh http add sslcert ipport=[::]:443 certhash=appid={ba195980-cd49-458b-9e23-c84ee0adcd75} certstorename=MY Restart the Routing and Remote Access service. The Routing and Remote Access service will read the certificate that is plumbed to the HTTPS Listener and record the certificate hash regkeys for its crypto-binding validation phase. See the "Restart Routing and Remote Access" section. Restart the Routing and Remote Access service To restart the Routing and Remote Access service: Open Routing and Remote Access. Click Start , click Run , type rrasmgmt.msc , and then press ENTER. In the console tree, click Server Status . In the details pane, right-click a server name, point to All Tasks , and click Restart . Verify : To verify that the remote access server can accept connections, establish a remote access connection from a client computer. To create a VPN connection: Click Start , and then click Control Panel . Click Network and Internet , click Network and Sharing Center , and then click Set up a connection or network . Click Connect to a workplace , and then click Next . Complete the steps in the Connect to a Workplace wizard. To connect to a remote access server: In Network and Sharing Center, click Manage network connections . Double-click the VPN connection, and then click Connect . Verify that the connection was established successfully. Numerous issues may impact Always On VPN administrators. Although many CVEs affect Always On VPN-related services that are Remote Code Execution (RCE) vulnerabilities, none are critical this cycle.RRAS UpdatesThis month, Microsoft has provided 12 updates for the Windows Server Routing and Remote Access Service (RRAS), commonly deployed to support Always On VPN deployments. Most of these CVEs involve overflow vulnerabilities (heap and stack), input validation weaknesses, and buffer over-read and overflow vulnerabilities. All are rated important, and there are no known exploits currently.CVE-2024-38212CVE-2024-38261CVE-2024-38265CVE-2024-43453CVE-2024-43549CVE-2024-43564CVE-2024-43589CVE-2024-43592CVE-2024-43593CVE-2024-43607CVE-2024-43608CVE-2024-43611Related UpdatesIn addition to the updates above, Microsoft also released fixes for security vulnerabilities in various related services that are important to Always On VPN administrators.Windows Network Address Translation (NAT)The following CVEs address denial of service vulnerabilities in the Network Address Translation (NAT) service.CVE-2024-43562CVE-2024-43565Certificate ServicesAlways On VPN administrators will also find updates for CVEs affecting various certificate services-related components.CVE-2024-43545 – OCSP Denial of Service VulnerabilityCVE-2024-43541 – Simple Certificate Enrollment Protocol (SCEP) Denial of Service VulnerabilityCVE-2024-43544 – Simple Certificate Enrollment Protocol (SCEP) Denial of Service VulnerabilityRecommendationsAlways On VPN administrators are encouraged to update systems as soon as possible. However, since none of the CVEs is rated Critical, updates can be applied during standard update windows.Additional InformationMicrosoft October 2024 Security Updates Posted in Active Directory Certificate Services, AD CS, Always On VPN, AOVPN, Certificate Authentication, Certificate Authority, Certificate Services, certificates, CVE, Enterprise, enterprise mobility, Hotfix, Mobility, NDES, Network Device Enrollment Service, Network Device Enrollment Services, PKI, Remote Access, routing and remote access service, RRAS, SCEP, Security, Simple Certificate Enrollment Protocol, Update, Vulnerability, Windows 10, Windows 11, Windows Server 2016, Windows Server 2019, Windows Server 2022, Windows Server 2025 Tagged Always On VPN, AOVPN, CVE, enterprise mobility, hotfix, Microsoft, Mobility, NDES, Network Device Enrollment Service, Patch Tuesday, RAS, Remote Access, Routing and Remote Access, routing and remote access service, RRAS, SCEP, security, Simple Certificate Enrollment Protocol, update, VPN, Windows, Windows Server Posted by Richard M. Hicks on October 8, 2024 Always On VPN May 2024 Security Updates Always On VPN RasMan Errors in Windows 10 1903" data-image-caption="" data-medium-file=" data-large-file=" src=" alt="Always On VPN RasMan Errors in Windows 10 1903">Once again, MicrosoftRouting and Remote Access Service
I can't get my desktop to connect to my laptop through remote desktop connection. Unfortunately I can only get my laptop to connect to my desktop (quite useless).Desktop:Windows 7 Ultimate 64 Bit SP1Windows firewall is off for all 3 profiles (domain / private / public)Remote desktop connection is installed and set to allow all connections Under running services is:Running Remote Desktop ConfigurationRunning Remote Desktop ServicesRunning Remote Desktop Services UserMode Port RedirectorRunning Remote Procedure Call (RPC)Stopped Remote Access Auto Connection ManagerStopped Remote Access Connection ManagerStopped Remote Procedure Call (RPC) LocatorStopped Remote RegistryStopped Routing and Remote AccessStopped Windows Remote Management (WS-Management)Laptop:Windows 7 Home Premium 64 Bit SP1Windows firewall is off for all3 profiles (domain / private / public)Remote desktop connection is installed and set to 'Allow Remote Assistance connections to this computer' Under running services is: Running Remote Procedure Call (RPC) Stopped Remote Access Auto Connection Manager Stopped Remote Access Connection Manager Stopped Remote Desktop Configuration Stopped Remote Desktop Services Stopped Remote Procedure Call (RPC) Locator Stopped Remote Registry Stopped Routing and Remote Access Stopped Windows Remote Management (WS-Management)It should be noted that the Laptop that I'm trying to connect to is an Alienware and might be running some wonky Dell settings. Also, the settings are slightly different for remote desktop connection as it's a Home edition of Windows and not Ultimate like my desktop.Finally, both computers are on the same Homegroup so that RDC can be accessed by one click through the network section of Windows. They're also on the same workgroup, MSHOME, just to see if that helps.. To resolve this behavior, stop the Routing and Remote Access service, start Remote Registry service, and then restart the Routing and Remote Access service. To do this To fix the routing and remote access service not starting. I have to restart the 'network policy server' service. Then start the 'routing and remote access' service. Routing andRouting and Remote Access Service (Routing) - Springer
Event Id20152SourceRemoteAccessDescriptionThe currently configured authentication provider failed to load and initialize successfully. %1Event Information According to Microsoft : Cause : This event is logged when currently configured authentication provider failed to load and initialize successfully. Resolution : Check the logs of the service To resolve this issue, check the logs of the services that provide accounting or authentication services to Routing and Remote Access. You can use event logging to record remote access server errors, warnings, and other detailed information in the system event log. To configure event logging: Open Routing and Remote Access. Click Start , click Run , type rrasmgmt.msc , and then press ENTER. Right-click the server name for which you want to view properties, and then click Properties . Click the Logging tab, and then configure event logging. Verify You can verify that Remote Access Connection Manager is working by checking the installation or service status. To check the status of the Remote Access Connection Manager service: Open Server Manager. In the navigation pane, double-click Diagnostics , and then click Services . In the details pane, verify that the Remote Access Connnection Manager service is installed and started. Note : If the Remote Access Connection Manager service does not appear in the list of services, you might need to repair or reinstall the operating system. If you cannot start the Remote Access Connection Manager service, try restarting the computer. Reference LinksEvent ID 20152 from RemoteAccess Catch threats immediately We work side-by-side with you to rapidly detect cyberthreats and thwart attacks before they cause damage. See what we caught Has released its monthly security updates. For May 2024, there are several vulnerabilities in services related to Always On VPN that administrators will want to pay close attention to. Microsoft has identified known issues in the Routing and Remote Access Service (RRAS) and the Remote Access Connection Manager (RasMan) service for this release cycle.RRASThis month, Microsoft published seven security fixes for vulnerabilities discovered in RRAS. All seven are Remote Code Execution (RCE) vulnerabilities rated Important. In addition, all vulnerabilities in RRAS require specific information about the environment for compromise, mitigating some of the exposure.CVE-2024-30009CVE-2024-30014CVE-2024-30015CVE-2024-30022CVE-2024-30023CVE-2024-30024CVE-2024-30029RasManIn addition to the updates for vulnerabilities in RRAS, Microsoft also released a security fix for issues identified in the Remote Access Connection Manager (RasMan) service. This update is marked Important but is not an RCE.CVE-2024-30039RecommendationsAlthough the vulnerabilities in RRAS are remotely exploitable, they will require specific information for an attacker to compromise. The risk of targeted attacks is lower than opportunistic ones, but administrators are still urged to update as soon as possible.Additional InformationMay 2024 Security Updates Posted in Always On VPN, AOVPN, enterprise mobility, Microsoft, Remote Access, routing and remote access service, RRAS, Security, Security Update, Update, VPN, Windows 10, Windows 11, Windows Server 2016, Windows Server 2019, Windows Server 2022 Tagged hotfix, Microsoft, rasman, Remote Access, Remote Access Connection Manager, routing and remote access service, RRAS, security, security update, update, vulnerability, Windows Posted by Richard M. Hicks on May 14, 2024Routing and Remote Access Service (RRAS)
Always On VPN Windows Server RRAS Service Does Not Start" data-image-caption="" data-medium-file=" data-large-file=" src=" alt="Always On VPN Windows Server RRAS Service Does Not Start" width="120" height="120">Administrators configuring a Windows Server Routing and Remote Access Service (RRAS) server to support Windows 10 Always On VPN connections may encounter an issue where the RemoteAccess service fails to start. Attempts to start the service might seem to work at first, but the service immediately stops again.TroubleshootingOn the RRAS server, the Services management console (services.msc) or PowerShell Get-Service command shows the RemoteAccess service as being stopped. Attempts to start the service result in failure.Always On VPN Windows Server RRAS Service Does Not Start" data-image-caption="" data-medium-file=" data-large-file=" src=" alt="Always On VPN Windows Server RRAS Service Does Not Start" width="600" height="326">Event LogLooking at the System event log on the RRAS server shows an error with event ID 7024 from the Service Control Manager source indicating “The Routing and Remote Access service terminated with the following service-specific error: A device attached to the system is not functioning.”Always On VPN Windows Server RRAS Service Does Not Start" data-image-caption="" data-medium-file=" data-large-file=" src=" alt="Always On VPN Windows Server RRAS Service Does Not Start" width="600" height="420">ResolutionThis issue is commonly caused when IPv6 is disabled on the server via the registry. To verify, open the registry editor on the RRAS server and navigate to the following location.HKLM\SYSTEM\CurrentControlSet\Services\Tcpip6\ParametersIf the DisabledComponents value is present and set to anything other than 0, set it to 0 or simply delete the DisabledComponents value completely and reboot the server.Always On VPN Windows Server RRAS Service Does Not Start" data-image-caption="" data-medium-file=" data-large-file=" src=" alt="Always On VPN Windows Server RRAS Service Does Not Start" width="600" height="152">The following PowerShell command can be used to remove the DisabledComponents value.Remove-ItemProperty HKLM:\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters -Name DisabledComponentsAdditional InformationIPv6 Recommended Reading for Always On VPN and DirectAccess AdministratorsGuidance for Configuring IPv6 in Windows for Advanced Users (Microsoft) Posted in Always On VPN, AOVPN, Enterprise, enterprise mobility, IPv6, PowerShell, Remote Access, routing and remote access service, RRAS, VPN, Windows 10, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016, Windows Server 2019 Tagged Always On VPN, AOVPN, enterprise mobility, event ID 7024, event log, IPv6, Microsoft, Mobility, PowerShell, Remote Access, routing and remote access service, RRAS, troubleshooting, VPN, Windows, Windows 10, Windows Server Posted by Richard M. Hicks on January 11, 2021Routing and Remote Access Service (RRAS) not
The Microsoft exam 70-291 measures an individual’s ability to implement, manage, and maintain a Microsoft Windows Server 2003 Network Infrastructure. Before taking the 70-291 exam, you should practice the following: Configure TCP/IP addressing on a server. Manage DHCP clients and leases, DHCP Relay Agent, DHCP databases, DHCP scope options, reservations and reserved clients. Diagnose and resolve issues related to Automatic Private IP Addressing (APIPA) and incorrect TCP/IP configuration. Diagnose and resolve issues related to DHCP authorization and verify DHCP reservation configuration. Diagnose and resolve issues related to configuration of DHCP server and scope options. Verify that the DHCP Relay Agent is working correctly and verify database integrity. Install and configure the DNS Server service. Configure DNS server options, DNS zone options, and forwarding. Configure DNS zone settings, DNS record settings, and DNS server options.Monitor DNS using tools such as System Monitor, Event Viewer, Replication Monitor, and DNS debug logs. Configure Routing and Remote Access user authentication and remote access authentication protocols. Configure Routing and Remote Access policies to permit or deny access.Configure Internet Authentication Service (IAS) to provide authentication for Routing and Remote Access clients.Manage TCP/IP routing. Manage routing protocols, routing tables, and routing ports. Monitor network traffic by using Network Monitor and System Monitor. Manage packet filters, Routing and Remote Access routing interfaces, manage devices and ports, manage routing protocols, and manage Routing and Remote Access clients. Post navigation. To resolve this behavior, stop the Routing and Remote Access service, start Remote Registry service, and then restart the Routing and Remote Access service. To do thisRouting and Remote Access Service - Wikipedia
Encrypt data.Components of a VPNA VPN in servers running Windows Server 2003 is made up of a VPN server, a VPN client, a VPN connection (that portion of the connection in which the data is encrypted), and the tunnel (that portion of the connection in which the data is encapsulated). The tunneling is completed through one of the tunneling protocols included with servers running Windows Server 2003, both of which are installed with Routing and Remote Access. The Routing and Remote Access service is installed automatically during the installation of Windows Server 2003. By default, however, the Routing and Remote Access service is turned off.The two tunneling protocols included with Windows are:Point-to-Point Tunneling Protocol (PPTP): Provides data encryption using Microsoft Point-to-Point Encryption.Layer Two Tunneling Protocol (L2TP): Provides data encryption, authentication, and integrity using IPSec.Your connection to the Internet must use a dedicated line such as T1, Fractional T1, or Frame Relay. The WAN adapter must be configured with the IP address and subnet mask assigned for your domain or supplied by an Internet service provider (ISP). The WAN adapter must also be configured as the default gateway of the ISP router.NoteTo turn on VPN, you must be logged on using an account that has administrative rights.How to install and turn on a VPN serverTo install and turn on a VPN server, follow these steps:Click Start, point to Administrative Tools, and then click Routing and Remote Access.Click the server icon that matches the local server name in the left pane of the console. If the icon has a red circle in the lower-left corner, the Routing and Remote Access service hasn't been turned on. If the icon has a green arrow pointing up in the lower-left corner, the Routing and Remote Access service has been turned on. If the Routing and Remote Access service was previously turn on, you may want to reconfigure the server. To reconfigure the server:Right-click the server object, and then click Disable Routing and Remote Access. Click Yes to continue when you're prompted with an informational message.Right-click the server icon, and then click Configure and Enable Routing and Remote Access to start the Routing and Remote Access Server Setup Wizard. Click Next to continue.Click Remote access (dial-up or VPN) to turn on remote computers to dial in or connect to this network through the Internet. Click Next to continue.Click to select VPN or Dial-up depending on theComments
Not for the sha256 Thumbprint algorithm. If there is mismtach between the hash of the certificate on the remote access server and the Web proxy server, right-click the certificate on the remote access server, and then click Delete . Remove the certificate binding from HTTPS Listener. Type the following commands in a command window: netsh http delete sslcert ipport=0.0.0.0:443 netsh http delete sslcert ipport=[::]:443 Remove the certificate binding in the Routing and Remote Access service. Open the Registry Editor and delete the following registry keys (if present): HKLM\System\CurrentControlSet\Services\Sstpsvc\Parameters\Sha256CertificateHash HKLM\System\CurrentControlSet\Services\Sstpsvc\Parameters\Sha1CertificateHash Add the new certificate inside the certificate store (local computer store). Plumb the new certificate to the HTTPS Listener (assuming the new certificate has SHA1 certificate hash as xxx). Type the following commands in a command window: netsh http add sslcert ipport=0.0.0.0:443 certhash= appid={ba195980-cd49-458b-9e23-c84ee0adcd75} certstorename=MY netsh http add sslcert ipport=[::]:443 certhash=appid={ba195980-cd49-458b-9e23-c84ee0adcd75} certstorename=MY Restart the Routing and Remote Access service. The Routing and Remote Access service will read the certificate that is plumbed to the HTTPS Listener and record the certificate hash regkeys for its crypto-binding validation phase. See the "Restart Routing and Remote Access" section. Restart the Routing and Remote Access service To restart the Routing and Remote Access service: Open Routing and Remote Access. Click Start , click Run , type rrasmgmt.msc , and then press ENTER. In the console tree, click Server Status . In the details pane, right-click a server name, point to All Tasks , and click Restart . Verify : To verify that the remote access server can accept connections, establish a remote access connection from a client computer. To create a VPN connection: Click Start , and then click Control Panel . Click Network and Internet , click Network and Sharing Center , and then click Set up a connection or network . Click Connect to a workplace , and then click Next . Complete the steps in the Connect to a Workplace wizard. To connect to a remote access server: In Network and Sharing Center, click Manage network connections . Double-click the VPN connection, and then click Connect . Verify that the connection was established successfully.
2025-04-06Numerous issues may impact Always On VPN administrators. Although many CVEs affect Always On VPN-related services that are Remote Code Execution (RCE) vulnerabilities, none are critical this cycle.RRAS UpdatesThis month, Microsoft has provided 12 updates for the Windows Server Routing and Remote Access Service (RRAS), commonly deployed to support Always On VPN deployments. Most of these CVEs involve overflow vulnerabilities (heap and stack), input validation weaknesses, and buffer over-read and overflow vulnerabilities. All are rated important, and there are no known exploits currently.CVE-2024-38212CVE-2024-38261CVE-2024-38265CVE-2024-43453CVE-2024-43549CVE-2024-43564CVE-2024-43589CVE-2024-43592CVE-2024-43593CVE-2024-43607CVE-2024-43608CVE-2024-43611Related UpdatesIn addition to the updates above, Microsoft also released fixes for security vulnerabilities in various related services that are important to Always On VPN administrators.Windows Network Address Translation (NAT)The following CVEs address denial of service vulnerabilities in the Network Address Translation (NAT) service.CVE-2024-43562CVE-2024-43565Certificate ServicesAlways On VPN administrators will also find updates for CVEs affecting various certificate services-related components.CVE-2024-43545 – OCSP Denial of Service VulnerabilityCVE-2024-43541 – Simple Certificate Enrollment Protocol (SCEP) Denial of Service VulnerabilityCVE-2024-43544 – Simple Certificate Enrollment Protocol (SCEP) Denial of Service VulnerabilityRecommendationsAlways On VPN administrators are encouraged to update systems as soon as possible. However, since none of the CVEs is rated Critical, updates can be applied during standard update windows.Additional InformationMicrosoft October 2024 Security Updates Posted in Active Directory Certificate Services, AD CS, Always On VPN, AOVPN, Certificate Authentication, Certificate Authority, Certificate Services, certificates, CVE, Enterprise, enterprise mobility, Hotfix, Mobility, NDES, Network Device Enrollment Service, Network Device Enrollment Services, PKI, Remote Access, routing and remote access service, RRAS, SCEP, Security, Simple Certificate Enrollment Protocol, Update, Vulnerability, Windows 10, Windows 11, Windows Server 2016, Windows Server 2019, Windows Server 2022, Windows Server 2025 Tagged Always On VPN, AOVPN, CVE, enterprise mobility, hotfix, Microsoft, Mobility, NDES, Network Device Enrollment Service, Patch Tuesday, RAS, Remote Access, Routing and Remote Access, routing and remote access service, RRAS, SCEP, security, Simple Certificate Enrollment Protocol, update, VPN, Windows, Windows Server Posted by Richard M. Hicks on October 8, 2024 Always On VPN May 2024 Security Updates Always On VPN RasMan Errors in Windows 10 1903" data-image-caption="" data-medium-file=" data-large-file=" src=" alt="Always On VPN RasMan Errors in Windows 10 1903">Once again, Microsoft
2025-04-03I can't get my desktop to connect to my laptop through remote desktop connection. Unfortunately I can only get my laptop to connect to my desktop (quite useless).Desktop:Windows 7 Ultimate 64 Bit SP1Windows firewall is off for all 3 profiles (domain / private / public)Remote desktop connection is installed and set to allow all connections Under running services is:Running Remote Desktop ConfigurationRunning Remote Desktop ServicesRunning Remote Desktop Services UserMode Port RedirectorRunning Remote Procedure Call (RPC)Stopped Remote Access Auto Connection ManagerStopped Remote Access Connection ManagerStopped Remote Procedure Call (RPC) LocatorStopped Remote RegistryStopped Routing and Remote AccessStopped Windows Remote Management (WS-Management)Laptop:Windows 7 Home Premium 64 Bit SP1Windows firewall is off for all3 profiles (domain / private / public)Remote desktop connection is installed and set to 'Allow Remote Assistance connections to this computer' Under running services is: Running Remote Procedure Call (RPC) Stopped Remote Access Auto Connection Manager Stopped Remote Access Connection Manager Stopped Remote Desktop Configuration Stopped Remote Desktop Services Stopped Remote Procedure Call (RPC) Locator Stopped Remote Registry Stopped Routing and Remote Access Stopped Windows Remote Management (WS-Management)It should be noted that the Laptop that I'm trying to connect to is an Alienware and might be running some wonky Dell settings. Also, the settings are slightly different for remote desktop connection as it's a Home edition of Windows and not Ultimate like my desktop.Finally, both computers are on the same Homegroup so that RDC can be accessed by one click through the network section of Windows. They're also on the same workgroup, MSHOME, just to see if that helps.
2025-04-04Event Id20152SourceRemoteAccessDescriptionThe currently configured authentication provider failed to load and initialize successfully. %1Event Information According to Microsoft : Cause : This event is logged when currently configured authentication provider failed to load and initialize successfully. Resolution : Check the logs of the service To resolve this issue, check the logs of the services that provide accounting or authentication services to Routing and Remote Access. You can use event logging to record remote access server errors, warnings, and other detailed information in the system event log. To configure event logging: Open Routing and Remote Access. Click Start , click Run , type rrasmgmt.msc , and then press ENTER. Right-click the server name for which you want to view properties, and then click Properties . Click the Logging tab, and then configure event logging. Verify You can verify that Remote Access Connection Manager is working by checking the installation or service status. To check the status of the Remote Access Connection Manager service: Open Server Manager. In the navigation pane, double-click Diagnostics , and then click Services . In the details pane, verify that the Remote Access Connnection Manager service is installed and started. Note : If the Remote Access Connection Manager service does not appear in the list of services, you might need to repair or reinstall the operating system. If you cannot start the Remote Access Connection Manager service, try restarting the computer. Reference LinksEvent ID 20152 from RemoteAccess Catch threats immediately We work side-by-side with you to rapidly detect cyberthreats and thwart attacks before they cause damage. See what we caught
2025-03-29