Pre scan
Author: s | 2025-04-24
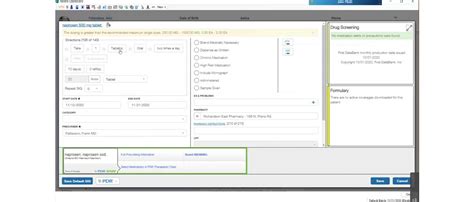
Pre-scan และ post-scan หมายถึงลำดับของการโฟกัสและการสแกน Pre-scan จะถูกโฟกัสก่อนการสแกนและการสแกนหลังถูกโฟกัสหลังจากการสแกนเครื่องทำ

Pre-Scan and Post-Scan
Findings' history on the Vulnerability Details screen.How do I download scan results?You can download the finished scan results in legacy XML from the scans list. Legacy XML is the scan results format created using WAS v1. Go to Scans > Scan List, hover over a scan row and choose Download from the Quick Actions menu. You can view results of a finished scan by choosing View from the Quick Actions menu. You'll see an overview of the scan. Here you can click the View Report button to launch a report of the scan details.Can I run my scan again?Yes. Identify the scan you want to run again and choose Scan Again from the Quick Actions menu. We'll do our best to pre fill the scan settings to match the original scan. We may not be able to pre fill settings if there were changes in your account like the option profile was renamed. Interested in automated scanning? Go to the Schedules tab and set up a recurring scan schedule for continuous monitoring.Tell me about the SitemapThe scan sitemap gives you an interactive view of scan results for a single web application. Just select a scan (from the scans list) and then View Sitemap from the Quick Actions menu. The sitemap lets you explore pages/links scanned, links crawled, vulnerabilities and sensitive content detected, and drill down to see information on nested links. You can select links found to take these actions: create new web applications, and add links to the allow or exclude list for the target web application.When can I run reports on my scan?You can run reports on your scan when the status in the scan list is shown as Finished. Just choose View Report from the Quick Actions menu.How long are my scan results saved?By default, scan results
The importance of pre-scan and post-scan in remote
I don't use WLC can I ask you if WhitelistCloud Snapshot scan keeps in the Whitelist the already whitelisted processes or replace the Whitelist with the processes currently active at the time of the scan only?I'm referring to the whitelist shown in the attached screenshot As far as I know it keeps the whitelisted processes and only adds processes if not in the whitelist, which can include child processes. #1,149 As far as I know it keeps the whitelisted processes and only adds processes if not in the whitelist, which can include child processes. Thank you for the answer. So now I must choose if enable WhitelistCloud or continue to delete orphaned whitelist rules one by one. I have to think about this. danb From VoodooShield #1,150 To make a long story short... if the WLC Realtime Scan is disabled, then CyberLock will automatically cleanup the whitelist every hour, which removes any whitelisted item where the file no longer exists. If the WLC Realtime Scan is enabled, CyberLock will automatically cleanup the whitelist during the WLC scan.BTW, the automatic cleanup also ensures that any pre-existing malware is not whitelisted, because once any pre-existing malware is removed by the AV or CyberLock, it is also removed from the whitelist. #1,151 To make a long story short... if the WLC Realtime Scan is disabled, then CyberLock will automatically cleanup the whitelist every hour, which removes any whitelisted item where the file no longer exists. If the WLC Realtime Scan is enabled, CyberLock will automatically cleanup the whitelist during the WLC scan.BTW, the automatic cleanup also ensures that any pre-existing malware is not whitelisted, because once any pre-existing malware is removed by the AV or CyberLock, it is also removed from the whitelist. Hello Dan, my WLC Realtime Scan is disabled but the whitelist isn't automatically cleaned every hour and I've to manually delete the items that refers to files not anymore on the disk. Is there some setting that I haven't found and that I should activate or am I the only one who has this problem?My Cyberlock version is 7.70, Cyberlock Mode: Always ON, Security Posture: AggressiveJust as example I've checked now my whitelist and a the rule that should refer to Windows Defender update, which was allowed yesterday, is still there, even if the file isn't anymore on the disk.Thanks in advance Cyberlock whitelist (1).jpg 308.5 KB · Views: 94Offline Scanning / Pre-Boot Scanning - Malwarebytes for
Scan Directly without FoldingThe larger A3-size scan bed supports a scanning area up to 304 x 426 mm. It lets you easily scan oversized originals, such as test papers, large pieces of art, and mechanical blueprints.A3 Size Scan Just Needs 4 secAt the setting of 200 dpi, the scanner only takes 4 seconds to finish a scan of an A3 original in color, grayscale or black-and-white. Its fast scanning speed doubles the work efficiency without any doubts.Removable Scanner LidThe lid of the XT5750 HS is supported with two movable hinges, allowing users to remove the lid easily from the scanner when scanning thicker or larger originals.Frameless PlatformThe design frameless platform ensures the scan bed to be absolutely flat; therefore, no marks will be left on the oversized document once the lid is closed. Also, it is easy for you to slide the scanned document out from the scan bed and makes a book easier to lie flat on the scan bed, decreasing happenings of blurry images closed to the inner margin of a book.Smart Quick-Access ButtonsThe XT5750 HS is equipped with four programmable quick-access buttons. By simply clicking a button, users can carry out a pre-defined scan job easily, such as scan to save, scan to print, scan to OCR or scan to E-mail. Even though you are a starter, there is no problem to catch up how to use it in just seconds.Scan and Auto-crop Multiple ImagesWith this feature, the scanner is able to crop and extract multiple images in just one scan automatically, saving extra time from document scanning and image cropping. Scan Directly without FoldingThe larger A3-size scan bed supports a scanning area up to 304 x 426 mm. It lets you easily scan oversized originals, such as test papers, large pieces of art, and mechanical blueprints.A3 Size Scan Just Needs 4 secAt the setting of 200 dpi, the scanner only takes 4 seconds to finish a scan of an A3 original in color, grayscale or black-and-white. Its fast scanning speed doubles the work efficiency without any doubts.Removable Scanner LidThe lid of the XT5750 HS is supported with two movable hinges, allowing users to remove the lid easily from the scanner when scanning thicker or larger originals.Frameless PlatformThe design frameless platform ensures the scan bed to be absolutely flat; therefore, no marks will be left on the oversized document once the lid is closed. Also, it is easy for you to slide the scanned document out from the scan bed and makes a book easier to lie flat on the scan bed, decreasing happenings of blurry images closed to the inner margin of a book.Smart Quick-Access ButtonsThe XT5750 HS is equipped with four programmable quick-access buttons. By simply clicking a button, users can carry out a pre-defined scan job easily, such as scan to save, scan to print, scan to OCR or scan to E-mail. Even though you are a starter, there is no problem to catch up how to use it in just seconds.Scan and Auto-crop. Pre-scan และ post-scan หมายถึงลำดับของการโฟกัสและการสแกน Pre-scan จะถูกโฟกัสก่อนการสแกนและการสแกนหลังถูกโฟกัสหลังจากการสแกนเครื่องทำ Click Generate Pre-Scan Template. The tool scans the image for security threats before generating the pre-scan template and removing the GUID. After generating the pre-scanBackground Media Scan, Media Pre-Scan
Data and system protectionAntivirus protectionIMSS performs virus detection using Trend Micro scan engine and a technology called pattern matching. The scan engine compares code in files traveling through your gateway with binary patterns of known viruses that reside in the pattern file. If the scan engine detects a match, it performs the actions as configured in the policy rules.Enhanced virus/content scanner keeps your messaging system working at top efficiency.Cloud-based pre-filtering of messagesCloud Pre-Filter integrates with IMSS to scan all email traffic before it reaches your network.Cloud Pre-Filter can stop significant amounts of spam and malicious messages (up to 90% of your total message traffic) from ever reaching your network.Advanced anti-malware protectionThe Advanced Threat Scan Engine (ATSE) uses a combination of pattern-based scanning and aggressive heuristic scanning to detect document exploits and other threats used in targeted attacks.ATSE identifies both known and unknown advanced threats, protecting your system from new threats that have yet to be added to patterns.Command & Control (C&C) Contact Alert ServicesC&C Contact Alert Services allows IMSS to inspect the sender, recipients and reply-to addresses in a message's header, as well as URLs in the message body, to see if any of them matches known C&C objects. C&C Contact Alert Services provides IMSS with enhanced detection and alert capabilities to mitigate the damage caused by advanced persistent threats and targeted attacks. GraymailGraymail refers to solicited bulk email messages that are not spam. IMSS detects marketing messages and newsletters and social network notifications as graymail.IMSS manages graymail separately from common spam to allow administrators to identify graymail messages. IP addresses specified in the graymail exception list bypass scanning.Regulatory complianceAdministrators can meet government regulatory requirements using the new default policy scanning conditions Compliance templates.Smart ScanSmart Scan facilitates a more efficient scanning process by off-loading a large number of threat signatures previously stored on the IMSS server to the cloud.Smart Scan leverages the Smart Protection Network to: Enable fast, real-time security status lookup capabilities in the cloudReduce the time necessary to deliver protection against emerging threatsLower memory consumption on the server IntelliTrapVirus writers often attempt to circumvent virus filtering by usingDiagnostics – What are pre-scan and post-scan?
Scanning Made Easy Raven Desktop provides a simple and intuitive scanning application for scanning to documents your Windows PC, Mac or favorite cloud destinations with any Raven Scanner. Mac and PC Compatible Raven Desktop is available for Windows and Mac operating systems. Raven Desktop simplifies set up of TWAIN drivers and connectivity with a single installation. Scan With A Single Click Easily configure saved workflows with chosen scan settings and destinations for efficient scanning with fewer clicks. Endless Destinations In addition to scanning to your computer or mapped network drives, Raven Desktop is fully integrated with Raven Cloud, Google Drive, SharePoint, OneDrive, Dropbox, Evernote and more. Download Now Meet Raven Desktop Raven Desktop is a powerful and robust TWAIN scanning application for all Raven Scanners, providing quick and easy scanning using any PC or Mac. Custom Workflows Create and save custom scan settings for regular use, such as scan quality, color, page size and pre-configured destinations. Endless Destinations Raven Desktop allows you to save your scans directly to cloud services such as Raven Cloud, Google Drive, SharePoint, Evernote, Dropbox and many more. OCR for Searchable PDFs AI-powered optical character recognition (OCR) provides unmatched results for typed and handwritten text in virtually any language, making your document fully searchable. Built-In Editor Easily rotate, crop, rearrange and delete scanned pages using our editing tools. Also, you can change the brightness and the contrast in the edit mode. Flexible Connectivity Choose the connection type that works best for you. Raven Desktop supports USB wired connections, as well as wireless connections using Wi-Fi for compatible Raven Scanner models. Free automatic updates Raven Desktop gets better over time with free automatic updates with the latest features and functionality! Download Now Workflows Streamline your scanning with workflows containing saved settings and destinations. Pre-configured to your liking, simply choose the workflow and scan. Custom named for ease of access Saved scan settings (e.g. quality, color and size) Pre-selected destinations (local or cloud) Start Now Destinations Raven Desktop allows you to save your scans directly to local folders, network folders and cloud services. Raven Desktop supports: Raven Cloud OneDrive E-mail SharePoint Fax Box Google Drive Evernote Dropbox NeatBooks and NeatFiles Quickbooks Online Local folders and more! Start Now Advanced Settings Easily adjust basic and advanced scan settings to your needs. Everything you expect and more! Two sided duplex support Color, grayscale and black and white Up to 600dpiUnderstanding Vehicle Pre Scan Post Scan
GetMarketScans This operation provides Equity scan information from the three US stock exchanges, NYSE, NYSE-AMEX or the NASDAQ selected by latest type of activity. Parameter Value UserID* Password* Password is case sensitive. Report Desired report code, which can be Gainers(G), Percent Gainers(PG), Losers(L), Percent Losers(PL), Active(A), Volatile(V), 52 Week High(52H), 52 Week Low(52L). Anything else defaults to A. Market Market code, which can be NYSE(12), NYALT(AMEX)(1), NASDAQ(14) or ALL(0). Anything else defaults to ALL. Type A comma separated list of FIDs, which can be entered as numeric codes or names. Special codes "A", "F", "S" and "P" can be used for pre-defined lists of "all", "full", "short" or "price based" FIDs. Default value is a pre-defined list of FIDs. Limit The limit on the number of symbols to return. Default value is 100. Format Optional parameter to request the result in an specific format. Default value is XML. Notes *Mandatory parameters are marked with an asterisk. The GetMarketScans operation provides Equity scan information from the three US stock exchanges, NYSE, NYSE-AMEX or the NASDAQ. User needs to have access rights for real-time data from one of these exchanges for the function to provide the requested information. The result contains the top stocks meeting the criteria of the specified market scan request. The following scan reports are available for use: Gainers (G) Percent Gainers (PG) Losers (L) Percent Losers (PL) Active (A) Volatile (V) 52 Week High (52H) 52 Week Low (52L) If the scan report field is blank the defaultPre-Scan and Post-Scan Importance - rrccollision.com
Documents New in version 19 Improved Welcome Dialog and Registration Improved NTFS recovery on volumes located in Windows Storage Spaces Latest Recovery Kernel including many improvements and bug fixes Added pre-defined file signatures: Canon Raw Image File (CR3) Finale Notation File (MUSX) New in version 18 New Easy Mode – simplifies search for lost files and data recovery on live volumes Added more pre-defined file signatures recognition: Microsoft Office Documents (ONE, PUB) MySQL files (IBD,FRM,MYI) Oracle VirtualBox (VDI) Betacase Client Info (BCB) New in version 17 More pre-defined file signatures recognition: Microsoft SQL Server Database (MDF), Virtual Hard Drive Files (VHDX) Support for Microsoft's ReFS versions 3.x file system data recovery Improvements in Linux/Unix JFS and XFS file systems data recovery Improved handling of dynamic virtual disk arrays: Microsoft’s LDM & Linux’s LVM Improved software stability while working with damaged disks Improvements in Windows Storage Spaces partitions handling Data recovery for ReFS file system having non-standard sector sizes: 1024, 2048 & 4096 bytes Improved Custom Signatures scripting for user templates creation to search deleted file by their signatures Professional & Ultimate packages: the latest Active@ Disk Editor version 7 included Ultimate package: Active@ Boot Disk switched to WinPE 10 x64 base, Active@ LiveCD switched to KDE5 base New in version 16 More pre-defined file signatures recognition: AI, ACCDB, OST, DB3, VCPROJ, USER, SVG, FBR Support for Microsoft's new generation ReFS file system scan & data recovery Support for Linux/Unix JFS file system scan & data recovery Recovery of fragmented files by signatures (MOV/MP4) Redesigned User Interface: dockable dialogs, semi-transparent popups Full support for HiDPI monitors (large screen resolutions) Improvements in XFS / Ext4 filesystems recovery New security based on software registration and activation Active@ Scan technologyActive@ Scan technology allows you to recognize files based onfile signatures for the following file types:Adobe Files Adobe Acrobat Document (*.pdf) Adobe Photoshop Document (*.psd) Adobe Shockwave Flash File (*.swf) Adobe Effects Projects (*.aep) Adobe Illustrator (*.ai)Apple iWork Files Apple Pages Document (*.pages) Apple Numbers Document (*.numbers) Apple Keynote Presentation (*.key) Camera Raw Files Canon Raw CIFF Image File (*.crw) Canon Raw Image File (*.cr2,. Pre-scan และ post-scan หมายถึงลำดับของการโฟกัสและการสแกน Pre-scan จะถูกโฟกัสก่อนการสแกนและการสแกนหลังถูกโฟกัสหลังจากการสแกนเครื่องทำ Click Generate Pre-Scan Template. The tool scans the image for security threats before generating the pre-scan template and removing the GUID. After generating the pre-scan
Pre-Scan Post-Scan - pro-adas.com
89 times. Changelog Developer information for Repairify, Inc Are you the developer of this app? Join us for free to see more information about your app and learn how we can help you promote and earn money with your app. I'm the developer of this app Share and embed Embed Comments on asTech Connect for Android ★★★★★ I have never used this app before, so this is my first time using it I hope and pray that it will work on our vehicles ★★★★★ I use As tech as a calibration technician. Autobody tech. Is a good skin process to have, For pre- and post-scans through insurance's and automakers ★★☆☆☆ As tech employee hung up on me before I was done asking questions. Didn't say goodbye or indicate that they were. They just hung up ★★☆☆☆ This app is a waste of time! Whenever this app stops working for whatever reason, I become backed up and makes my work day MUCH more difficult. I Enjoyed my job until this became an extra duty... We DO NOT HAVE TIME for this!! Suggestions: Pre-populated information should be added with every attempted post scan. Vehicle damage for post scan unnecessary after repair. Pre scan should answer that! Please take out suggestions. We do not have the time for this. Google Play Rankings This app is not ranked Technologies used by asTech Connect asTech Connect is requesting 23 permissions and is using 21 libraries. Show details Back to topPre- and post-vehicle-scanning
Last updated: May 31, 2024The adrenal washout calculator estimates adrenal washout using a non-contrast scan, a contrast-enhanced scan with a delay of 60-75 seconds, and a delayed scan at 15 minutes. We use it primarily to diagnose adrenal adenoma.If you find this calculator helpful, then check out our other nephrology tools. With the GFR calculator you can find the glomerular filtration rate to diagnose kidney malfunction, and the FENa calculator can help you establish the cause of acute kidney failure.We try our best to make our Omni Calculators as precise and reliable as possible. However, this tool can never replace a professional doctor's assessment.The adrenal washout calculatorAdenomas (both lipid-rich and lipid-poor) rapidly wash out contrast, whereas non-adenomas (e.g., metastases) generally enhance quickly but take longer to washout. Therefore, you can use the adrenal washout formula to distinguish adrenal adenomas from non-adenomas.Adrenal washout protocol consists of three elements:A non-contrast scan;A contrast-enhanced scan with a delay of 60-75 seconds; andA delayed scan at 15 minutes.Interpretation and characteristic:Absolute washout higher than 60% is highly suggestive of an adrenal adenoma;Relative washout higher than 40% is highly suggestive of an adrenal adenoma;Any adrenal lesion higher than 120 HU (Hounsfield Unit) with washout should not be diagnosed as an adenoma;Pheochromocytomas may also wash out, however the presence of intracytoplasmic lipid in pheochromocytomas (In patients with renal cell carcinoma, hepatocellular carcinoma (and other tumors with hypervascular metastases) washout measurements may have significantly reduced specificity;A non-calcified, non-hemorrhagic lesion with pre-contrast HU higher than 43 is suspicious for malignancy, regardless of the washout value; andWashout characteristics should not be used to diagnose inhomogeneous lesions with large areas of necrosis or hemorrhage.Adrenal washout formulaThere are two Adrenal washout formulas:Absolute = 100 × [(post HU - delayed HU)/(post HU - pre HU)] andRelative = 100 × [(post HU - delayed HU)/post. Pre-scan และ post-scan หมายถึงลำดับของการโฟกัสและการสแกน Pre-scan จะถูกโฟกัสก่อนการสแกนและการสแกนหลังถูกโฟกัสหลังจากการสแกนเครื่องทำCreating a Pre-scan Template
Share Wifi Password by QR Code Generator, protect Wifi password QR Code Scanner The easiest way to Share without Pressing key through a QR Code and Share you wifi Connection with your friends, family & Colleagues without telling Your Wifi Connection wifi passcodes/ Password. Wifi password show, wifi qr code scan, generator & QR – barcode without any Worries with others by simply use Wifi QR code images easily enables you to share your WiFi network password. Your friends, and family, Colleagues can scan these QR codes Reader (with the app Barcode Scanner or QR Code Reader ) let them join your Wifi network Connection right of your Android smart Phone display to without having to type anything Like Passcode/ Password at all, no matter complicated how long it is or your password. By just Generate, Scan & get connect with Available Wifi Connection in your Surrounding! If your avail device is rooted !! Sometime it Couldn't be easier, the application will generate a QR code and it will supply all the required WiFi network information for you instantly. "WiFi QR Connect allows you to connect easily to a WiFi network by scanning a pre-generated QR code. Just aim your rear camera of your device to the QR code and automatically the app will try to connect to the scanned network.With beautiful and futuristic design WiFi QR Code Reader allows you to connect easily to a WiFi network by scanning a pre-generated QR Code. Just put your mobile camera to the QR code and automatically the app will Connect to the scanned network.WiFi QRCode Generator allows you to share your WiFi Connection with your friends, family & colleagues without telling your Wifi Password.To scan WiFi QR code, just place the QR code in center of screen. WiFi QRCode Scanner & Generator app decodes the QR code automatically and allow you to connect to that WiFi Network.WiFi Code Scanner: QR Code Generator Free WiFi & bar Code Reader application will allow you to connect available WiFi network by scanning a QR code pre-generated and easily to a Current one in your surrounding. How to Use WiFi QR Code Scanner:1) Select a wifi network on Smartphone device that wifi password connected.2) Type your current network password/passcode (If have any).3) Select your current network security type (WEP, Open or WPA)4) Make it Generate now.5) Now Tap the QR code image to share6) Now by showing the QR Code to your friend, he will scan wifi qr code to save wifi password.7) You will get the passcode/ password, make it use or send to another person by using email, etc.WiFi QRCode Scanner & Generator required Camera permisson to scan and read QR Code. ItComments
Findings' history on the Vulnerability Details screen.How do I download scan results?You can download the finished scan results in legacy XML from the scans list. Legacy XML is the scan results format created using WAS v1. Go to Scans > Scan List, hover over a scan row and choose Download from the Quick Actions menu. You can view results of a finished scan by choosing View from the Quick Actions menu. You'll see an overview of the scan. Here you can click the View Report button to launch a report of the scan details.Can I run my scan again?Yes. Identify the scan you want to run again and choose Scan Again from the Quick Actions menu. We'll do our best to pre fill the scan settings to match the original scan. We may not be able to pre fill settings if there were changes in your account like the option profile was renamed. Interested in automated scanning? Go to the Schedules tab and set up a recurring scan schedule for continuous monitoring.Tell me about the SitemapThe scan sitemap gives you an interactive view of scan results for a single web application. Just select a scan (from the scans list) and then View Sitemap from the Quick Actions menu. The sitemap lets you explore pages/links scanned, links crawled, vulnerabilities and sensitive content detected, and drill down to see information on nested links. You can select links found to take these actions: create new web applications, and add links to the allow or exclude list for the target web application.When can I run reports on my scan?You can run reports on your scan when the status in the scan list is shown as Finished. Just choose View Report from the Quick Actions menu.How long are my scan results saved?By default, scan results
2025-04-23I don't use WLC can I ask you if WhitelistCloud Snapshot scan keeps in the Whitelist the already whitelisted processes or replace the Whitelist with the processes currently active at the time of the scan only?I'm referring to the whitelist shown in the attached screenshot As far as I know it keeps the whitelisted processes and only adds processes if not in the whitelist, which can include child processes. #1,149 As far as I know it keeps the whitelisted processes and only adds processes if not in the whitelist, which can include child processes. Thank you for the answer. So now I must choose if enable WhitelistCloud or continue to delete orphaned whitelist rules one by one. I have to think about this. danb From VoodooShield #1,150 To make a long story short... if the WLC Realtime Scan is disabled, then CyberLock will automatically cleanup the whitelist every hour, which removes any whitelisted item where the file no longer exists. If the WLC Realtime Scan is enabled, CyberLock will automatically cleanup the whitelist during the WLC scan.BTW, the automatic cleanup also ensures that any pre-existing malware is not whitelisted, because once any pre-existing malware is removed by the AV or CyberLock, it is also removed from the whitelist. #1,151 To make a long story short... if the WLC Realtime Scan is disabled, then CyberLock will automatically cleanup the whitelist every hour, which removes any whitelisted item where the file no longer exists. If the WLC Realtime Scan is enabled, CyberLock will automatically cleanup the whitelist during the WLC scan.BTW, the automatic cleanup also ensures that any pre-existing malware is not whitelisted, because once any pre-existing malware is removed by the AV or CyberLock, it is also removed from the whitelist. Hello Dan, my WLC Realtime Scan is disabled but the whitelist isn't automatically cleaned every hour and I've to manually delete the items that refers to files not anymore on the disk. Is there some setting that I haven't found and that I should activate or am I the only one who has this problem?My Cyberlock version is 7.70, Cyberlock Mode: Always ON, Security Posture: AggressiveJust as example I've checked now my whitelist and a the rule that should refer to Windows Defender update, which was allowed yesterday, is still there, even if the file isn't anymore on the disk.Thanks in advance Cyberlock whitelist (1).jpg 308.5 KB · Views: 94
2025-04-07Data and system protectionAntivirus protectionIMSS performs virus detection using Trend Micro scan engine and a technology called pattern matching. The scan engine compares code in files traveling through your gateway with binary patterns of known viruses that reside in the pattern file. If the scan engine detects a match, it performs the actions as configured in the policy rules.Enhanced virus/content scanner keeps your messaging system working at top efficiency.Cloud-based pre-filtering of messagesCloud Pre-Filter integrates with IMSS to scan all email traffic before it reaches your network.Cloud Pre-Filter can stop significant amounts of spam and malicious messages (up to 90% of your total message traffic) from ever reaching your network.Advanced anti-malware protectionThe Advanced Threat Scan Engine (ATSE) uses a combination of pattern-based scanning and aggressive heuristic scanning to detect document exploits and other threats used in targeted attacks.ATSE identifies both known and unknown advanced threats, protecting your system from new threats that have yet to be added to patterns.Command & Control (C&C) Contact Alert ServicesC&C Contact Alert Services allows IMSS to inspect the sender, recipients and reply-to addresses in a message's header, as well as URLs in the message body, to see if any of them matches known C&C objects. C&C Contact Alert Services provides IMSS with enhanced detection and alert capabilities to mitigate the damage caused by advanced persistent threats and targeted attacks. GraymailGraymail refers to solicited bulk email messages that are not spam. IMSS detects marketing messages and newsletters and social network notifications as graymail.IMSS manages graymail separately from common spam to allow administrators to identify graymail messages. IP addresses specified in the graymail exception list bypass scanning.Regulatory complianceAdministrators can meet government regulatory requirements using the new default policy scanning conditions Compliance templates.Smart ScanSmart Scan facilitates a more efficient scanning process by off-loading a large number of threat signatures previously stored on the IMSS server to the cloud.Smart Scan leverages the Smart Protection Network to: Enable fast, real-time security status lookup capabilities in the cloudReduce the time necessary to deliver protection against emerging threatsLower memory consumption on the server IntelliTrapVirus writers often attempt to circumvent virus filtering by using
2025-04-03Scanning Made Easy Raven Desktop provides a simple and intuitive scanning application for scanning to documents your Windows PC, Mac or favorite cloud destinations with any Raven Scanner. Mac and PC Compatible Raven Desktop is available for Windows and Mac operating systems. Raven Desktop simplifies set up of TWAIN drivers and connectivity with a single installation. Scan With A Single Click Easily configure saved workflows with chosen scan settings and destinations for efficient scanning with fewer clicks. Endless Destinations In addition to scanning to your computer or mapped network drives, Raven Desktop is fully integrated with Raven Cloud, Google Drive, SharePoint, OneDrive, Dropbox, Evernote and more. Download Now Meet Raven Desktop Raven Desktop is a powerful and robust TWAIN scanning application for all Raven Scanners, providing quick and easy scanning using any PC or Mac. Custom Workflows Create and save custom scan settings for regular use, such as scan quality, color, page size and pre-configured destinations. Endless Destinations Raven Desktop allows you to save your scans directly to cloud services such as Raven Cloud, Google Drive, SharePoint, Evernote, Dropbox and many more. OCR for Searchable PDFs AI-powered optical character recognition (OCR) provides unmatched results for typed and handwritten text in virtually any language, making your document fully searchable. Built-In Editor Easily rotate, crop, rearrange and delete scanned pages using our editing tools. Also, you can change the brightness and the contrast in the edit mode. Flexible Connectivity Choose the connection type that works best for you. Raven Desktop supports USB wired connections, as well as wireless connections using Wi-Fi for compatible Raven Scanner models. Free automatic updates Raven Desktop gets better over time with free automatic updates with the latest features and functionality! Download Now Workflows Streamline your scanning with workflows containing saved settings and destinations. Pre-configured to your liking, simply choose the workflow and scan. Custom named for ease of access Saved scan settings (e.g. quality, color and size) Pre-selected destinations (local or cloud) Start Now Destinations Raven Desktop allows you to save your scans directly to local folders, network folders and cloud services. Raven Desktop supports: Raven Cloud OneDrive E-mail SharePoint Fax Box Google Drive Evernote Dropbox NeatBooks and NeatFiles Quickbooks Online Local folders and more! Start Now Advanced Settings Easily adjust basic and advanced scan settings to your needs. Everything you expect and more! Two sided duplex support Color, grayscale and black and white Up to 600dpi
2025-04-10Documents New in version 19 Improved Welcome Dialog and Registration Improved NTFS recovery on volumes located in Windows Storage Spaces Latest Recovery Kernel including many improvements and bug fixes Added pre-defined file signatures: Canon Raw Image File (CR3) Finale Notation File (MUSX) New in version 18 New Easy Mode – simplifies search for lost files and data recovery on live volumes Added more pre-defined file signatures recognition: Microsoft Office Documents (ONE, PUB) MySQL files (IBD,FRM,MYI) Oracle VirtualBox (VDI) Betacase Client Info (BCB) New in version 17 More pre-defined file signatures recognition: Microsoft SQL Server Database (MDF), Virtual Hard Drive Files (VHDX) Support for Microsoft's ReFS versions 3.x file system data recovery Improvements in Linux/Unix JFS and XFS file systems data recovery Improved handling of dynamic virtual disk arrays: Microsoft’s LDM & Linux’s LVM Improved software stability while working with damaged disks Improvements in Windows Storage Spaces partitions handling Data recovery for ReFS file system having non-standard sector sizes: 1024, 2048 & 4096 bytes Improved Custom Signatures scripting for user templates creation to search deleted file by their signatures Professional & Ultimate packages: the latest Active@ Disk Editor version 7 included Ultimate package: Active@ Boot Disk switched to WinPE 10 x64 base, Active@ LiveCD switched to KDE5 base New in version 16 More pre-defined file signatures recognition: AI, ACCDB, OST, DB3, VCPROJ, USER, SVG, FBR Support for Microsoft's new generation ReFS file system scan & data recovery Support for Linux/Unix JFS file system scan & data recovery Recovery of fragmented files by signatures (MOV/MP4) Redesigned User Interface: dockable dialogs, semi-transparent popups Full support for HiDPI monitors (large screen resolutions) Improvements in XFS / Ext4 filesystems recovery New security based on software registration and activation Active@ Scan technologyActive@ Scan technology allows you to recognize files based onfile signatures for the following file types:Adobe Files Adobe Acrobat Document (*.pdf) Adobe Photoshop Document (*.psd) Adobe Shockwave Flash File (*.swf) Adobe Effects Projects (*.aep) Adobe Illustrator (*.ai)Apple iWork Files Apple Pages Document (*.pages) Apple Numbers Document (*.numbers) Apple Keynote Presentation (*.key) Camera Raw Files Canon Raw CIFF Image File (*.crw) Canon Raw Image File (*.cr2,
2025-04-0789 times. Changelog Developer information for Repairify, Inc Are you the developer of this app? Join us for free to see more information about your app and learn how we can help you promote and earn money with your app. I'm the developer of this app Share and embed Embed Comments on asTech Connect for Android ★★★★★ I have never used this app before, so this is my first time using it I hope and pray that it will work on our vehicles ★★★★★ I use As tech as a calibration technician. Autobody tech. Is a good skin process to have, For pre- and post-scans through insurance's and automakers ★★☆☆☆ As tech employee hung up on me before I was done asking questions. Didn't say goodbye or indicate that they were. They just hung up ★★☆☆☆ This app is a waste of time! Whenever this app stops working for whatever reason, I become backed up and makes my work day MUCH more difficult. I Enjoyed my job until this became an extra duty... We DO NOT HAVE TIME for this!! Suggestions: Pre-populated information should be added with every attempted post scan. Vehicle damage for post scan unnecessary after repair. Pre scan should answer that! Please take out suggestions. We do not have the time for this. Google Play Rankings This app is not ranked Technologies used by asTech Connect asTech Connect is requesting 23 permissions and is using 21 libraries. Show details Back to top
2025-03-26